Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
Basic Online Safety Tips & Tricks
As the world becomes more reliant on technology, cyber criminals are constantly upgrading their methods to take advantage of our interconnected world. They have the means to target thousands of people in seconds and conduct large attacks, leaving little trace behind.
Cyber criminals also have the security of knowing that authorities only handle the biggest cases with the highest chances of conviction due to lack of resources.
That means if you were the victim of a cyber crime, you will more likely have to accept your loss or find a way to deal with it yourself.
This can cause emotional hardship and extreme stress, especially to those who are dealing with ongoing problems, such as hacked accounts, stolen identities, or online harassment.
You may feel relieved to know that most common cybersecurity risks are preventable, but that’s only if you take proper precautions in advance.
There are basic cybersecurity rules that are repeated time and time again but are often neglected by the general public. I wanted to explain why to these rules to further encourage you to take action before it’s too late.
1. Do Not Use A Basic Password

How to choose a strong password is the best question you can ask yourself and sometimes that is your only defence against many cybercrimes.
You need to not only protect your account, but also the private or sensitive information that may come with it.
Hackers have fast and powerful tools.
In combination with those tools, there are many word lists freely circulating the web that they can use to try to hack accounts. If your password is a common password or just a dictionary word, hackers will be able to figure out your password in under a minute through their methods.
A hacker may also break into a website and obtain a list of member information which could include your full name, email, username, and your password.
Lucky for users, passwords are encrypted as a unique ‘hash’ and are saved in the database that way. When you try to log in, the password you typed in is quickly hashed and compared to the hashed password on file. If it is a match, you get access. If not, you are denied access.
Since hashes can’t be decrypted, all you can do is reset your password if you forget it. But the site can still tell you if your new password matches the old one because the hashes would match.
This also means that there is no way for the hacker to figure out what your password is with just the hash, as it cannot be decrypted.
However, there are many lists on the internet that contain common passwords and their matching hashes. The more common your password is, the more likely it is that someone has already matched the hash to it and added it to a database or forum.
If your password is unique, it will not show up on those lists; and to crack a long, strong, and unique password could take months or even years to decrypt. Unless a hacker had something against you personally, you can feel safe in knowing that you are quite protected with a strong password.
Related Read: Best Password Managers
2. Do Not Use The Same Password For Everything
Upgrade your defences against dangerous cybersecurity risks by not using the same password for everything.
Adding onto the above, having the same password for everything will only make it easier for a hacker to take over all your accounts.
If you spend a moment to think about all the accounts you own that have the same password, you may realize how much power you are giving hackers if they manage to crack one of them.
These accounts may hold sensitive information, financial records, personal or private photos, important conversations, your home address, and much more. Hackers can then use this information to impersonate you, steal your identity, scam your friends, and even extort you.
It can be hard or even impossible to create a new, strong, and unique password for every online account you have, but luckily you don’t have to to stay safe.
What I would recommend is, at the bare minimum, have two root emails that each have its own strong unique password. Use one email for your finances and sensitive accounts, and the other for social media and other online activity.
The reason I recommend focusing on your emails is because they are your most important online asset.
All your other online accounts are connected to it. Your email is also the only way to restore those accounts if you were hacked or forgot your password.
If a hacker gains access to your email, not only will you not be able to save your other accounts, but they can also access everything else that is attached to your email, along with all the contents of your inbox.
Although you may be able to contact your email provider or find another way to get back into your inbox, a lot of damage can be done in a little amount of time. Sometimes, you will never get these accounts back and you’ll just have to start over.
Ideally, you should use a secure email provider and not take any chances when it comes to the security of your email.
Related Read: Fight Common Java Security Vulnerabilities from DevOps
3. Do Not Share Certain Personal Information Online

Another method hackers use to gain access to your accounts is through intelligence.
Hackers can gain a lot of information through research, and can sometimes guess what someone’s password would be, as many people use their birthdate, favourite character, or the name of a lover as their password.
They could also avoid passwords altogether and try to gain access by answering security questions. Security questions usually ask for basic information such as your elementary school, your first pet’s name, or your favourite food.
These are things someone would tell or share publicly without a second thought as it is not necessarily something to hide. However, some of these things you should never post online.
Youth tend to be more open about putting their lives out there on social media. If they are an active user with many profiles, their digital footprint can become an autobiography, full of personal information, likes, interests, connections, and history. People may post about their birthday, make an RIP post remembering their first pet, or just share about things they love openly. Through photos and geolocation, hackers could even pinpoint their home address.
Thus, if you can keep your life more private, please do so. If you are an online personality and feel the need to be more transparent, just keep an eye on your security questions and make sure not to reveal those answers. If you have the option to create a privacy question, think of something you would easily remember but would have no reason to share, like the middle name of your second favourite cousin.
4. Don’t Accept Friend Requests From Strangers
A seemingly innocent friend request can turn your life upside down. While youth may be more likely to share personal details openly, the older generation have a habit of adding strangers online.
What people need to realize is that, even with the strongest security settings, your defense goes out the window once you accept a stranger as your friend. You also put your friends and family at risk as they may have their securities settings set for ‘friends of friends’, or may be more open to accepting someone with a mutual friend.
Adding on to the list above about what cyber criminals can do with your personal information, they can also impersonate someone in your circle and send malicious links to everyone, plan a robbery when they know someone is away from home, build a relationship with the intent of getting money (romance scam), or try to get you to meet with them one day in an attempt to kidnap you (human trafficking). The list goes on.
If you are interested in making new friends, it is better to meet people in person, and safer through a dedicated friendship/dating app. Just don’t add them to your personal social media account before you get to know them as people aren’t always what they seem.
5. Avoid Connecting to Public Wifis

When connecting to a public wifi connection, you may have been given a warning informing you that the network is unsecure and that others can see what you are doing.
Wifi works like a two-way radio (or a walkie-talkie). Every device connected to the same network is on the same channel, and all devices are sending broadcasts everywhere to ensure it reaches the intended recipient faster.
This means your device is picking up these broadcasts sent from other devices; but since it is not the intended recipient, your device ignores it. The same happens for all the other devices on the network. There are, however, free network sniffing tools that allow any device to actually collect all these broadcasts in one place and see what data is being sent and where it’s headed.
Lucky for us, data is sent through many smaller packets instead of one big package. Thus, it could be hard for someone to figure out exactly what you are doing with just a handful of packets; but they may also get lucky and receive a packet that contains your log-in credentials or banking information if you just happen to be signing in or buying something at that moment.
Another risk to using public wifi is that cyber criminals may create a rogue wifi connection that looks authentic or replaces the one you’ve used before. If you connect to these hotspots, cyber criminals can actually access your device, forward you to fake websites, steal your files, upload malware, and much more.
Thus, avoid public wifi if possible. If you must use it, avoid logging in to websites or performing any financial transactions while connected. If you rely on public wifi or use it regularly, it may be worth looking into a quality VPN. A VPN is software installed onto your device. When activated, it creates a personal private network that encrypts everything you do on the net, hiding it from possible snoopers and even your ISP.
6. Avoid Opening Spam Mail And Don’t Click On It’s Contents
A decade ago, scams used to consist of winning the lottery and the infamous Nigerian prince who wanted to give you his money; but nowadays, scammers are impersonating big brands, your local bank, and even the CRA. It can be easy to fall for these if your guard isn’t up at all times.
Although a simple email may seem innocent, just opening the email can alert the scammer that you’ve seen it, and they can collect further information such as your city, IP address, and the browser via a canary or honey token. If they know your email is active, they may keep it and share it, and thus you will receive even more spam in the future.
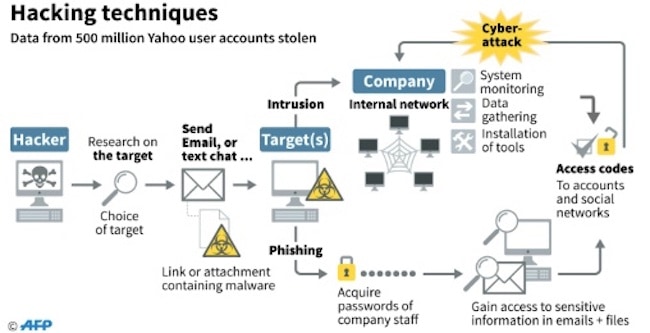
If you click on a link provided and sign in to the webpage you are forwarded too, you are more likely sending your log-in credentials to the scammer, as the website is probably a fake copy. If you call the number provided, it will lead to the scammers themselves where they can convince you further that they are real, and demand payment or further action.
Hackers can also use links or attachments that, when clicked, will silently download malware and give them full access to your device. They can then steal your documents, track what you do, spy on you through your webcam, and much, much more. They can also install ransomware which will lock off your computer and encrypt your files, holding it for ransom in exchange for money.
Related: Best Malware Scanner
Therefore, I would recommend avoiding any email that looks fishy, especially if you are not expecting it. If you do open it, do not click on anything unless you are 100% sure it is from the real person or company. If you want to see if the contents of the email are real or fake, open the website yourself or call a trusted number, instead of using what was provided in the email.
Always keep your guard up and look for red flags such as poor writing and weird email addresses. Never act or respond to threats. If it was serious, the company would call you or send you a letter. They would not give you a 48-hour deadline through an email that you may not see in time. Lastly, remember the saying that “If it sounds too good to be true, it probably is.”
See also: Cybersecurity Skill Gap
Conclusion
Hackers and scammers are constantly upgrading their methods and educating themselves, so we must also do the same with our defenses if we want to stay safe online.
Even if you have the best security settings and anti-virus installed, it only takes one negligent click on your part to bypass all that. Human ignorance is the easiest way for cyber criminals to gain access, money, and power over your life.
Take action today by changing your passwords, enforcing your defense, and taking any cyber security tips to heart. Be sure to inform your loved ones so they too can be ready and alert.
Let’s work together so fewer people become cyber crime victims.





