Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
Common Cybersecurity Threats
Not long after Canadians welcomed the year 2024, reports about major cyber attacks started to dominate news headlines.
On January 6, CTV reported that the Twitter account of Senator Linda Frum, a Conservative who represents Ontario, was taken over by members of the “Spank Gang,’ a cybercrime group known to target politicians in Europe and North America. Senator Frum’s driver’s licence and personal information were posted on her Twitter account along with messages that suggested corruption.
Less than 10 days after the aforementioned attack, the Nova Scotia Department of Internal Services published a report about a serious data breach suffered in 2018 after hackers stole thousands of documents from the provincial Freedom of Information Access website, thus compromising the personal records of more than 700 Canadians.
This report is being closely followed by information security experts because it involved not just a network intrusion but also a breach of a case management system used by government agencies.
Compared to internet users in the rest of the Americas and Europe, Canadians have an interesting relationship with information technology. While the rate of technology adoption has grown across the provinces, people in Canada tend to be more guarded about their personal information when compared to their neighbors to the south.
Americans seem to be more willing to accept the loss of privacy as the cost of technology advancement; on the other hand, Canadians are more likely to learn about online privacy and protect it when they browse the web. For the most part, this cautious attitude towards internet technology has paid off: the massive data breaches that the United States seems to suffer on a daily basis are not as common or as damaging in Canada.
With the above in mind, internet users in Canada deserve to learn about the cyber risks that they may face in 2024. Here are the 10 most dangerous situations determined by the Department of Public Safety and Emergency Preparedness and by leading information security researchers:
1. Zero-Day Exploits
In January 2020, an unidentified computer virus infected the Health Sciences North network in Ontario, forcing more than 20 hospitals to shut down their IT platforms in an effort to prevent the malware from spreading further.
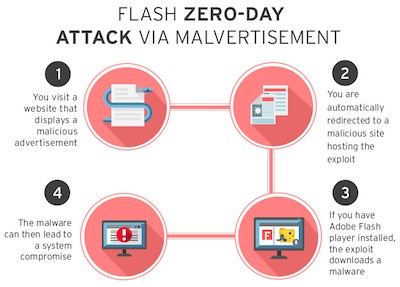
The virus was reported by CBC news as a “zero-day” exploit, which means that it is a new exploit that slipped past installed antivirus software. Cybercrime groups take pride in discovering new exploits that defeat security measures; these so-called zero-day exploits are becoming more sophisticated and could pose a significant threat in 2024.
2. Phishing
Of all the known cyber security risks, this is one of the easiest for talented hackers to deploy, and it can be one of the most damaging to local businesses and their reputation.
Phishing has its roots in a malicious practice known as social engineering; in the past, the most daring hackers ventured away from their desks and went out in the field to obtain valuable information such as username and password credentials directly from unsuspecting victims. A common strategy in this regard involved making phone calls pretending to be technicians who need information in order to complete a task.

Phishing is the natural evolution of social engineering, and it has proven to be very effective in the 21st century because it is commonly deployed by means of fake emails, text messages or phony websites that look just like the real thing. Research research from IAPP shows that anywhere from 84 to 92 percent of data breaches are due to negligence / human error, making social engineering-driven phishing a popular attack vector among cyber criminals.
Remember the intrusion of the Democratic Party email system during the scandalous 2016 American election?
That entire ordeal started with a phishing email sent to politicians who believed Google had sent them a security alert. The email in question was designed to look exactly like a Gmail security notification, and the targets unknowingly surrendered their email credentials to Russian hackers.
It should be noted that old school hackers believe that phishing is beneath them, though some will not think twice about calling you pretending to be Roger, a cable technician who needs to get the password to your wireless router.
3. Botnets
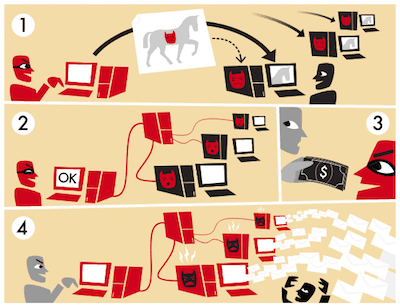
Computing devices can be easily conscripted into botnets for malicious purposes. In many cases, users are not aware that their desktops, laptops, tablets, smartphones, routers, printers, or even smart refrigerators have been forced to join a botnet.
Botnets were created in the 1990s to augment internet relay chat networks, but it did not take long for hackers to devise ways to illegally organize them. In 2024, the botnet threat is set to grow considerably because of the popularity of smart home automation devices that connect to the internet. The poor security inherent in many of these devices makes them more vulnerable to botnet conscription. (Check out this 2-minute video)
4. Distributed Denial of Service Attacks
In April 2018, the Royal Canadian Mounted Police raided a Toronto data centre identified by information security investigators as being part of a cybercrime group that offered DDoS attacks for hire. In essence, DDoS attacks involve the malicious take-down of an internet-connected device or service.
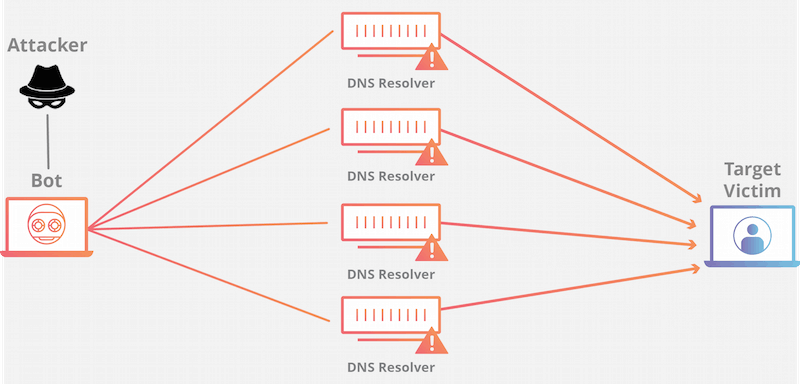
This is accomplished by means of routing massive amounts of traffic to the target. While websites and commercial networks are the most commonly affected by DDoS attacks, individual computers and even smartphones can also be targeted. One of the most common strategies applied in DDoS attacks consists of using botnets.
5. Spam
Even though Canada has adopted legislation to prohibit the distribution of commercial messages without previous solicitation, spam is a global issue that continues to worsen.
Spam emails and messages are not just nuisances; they can be weaponized for the purpose of distributing malware that steals personal information or recruits personal computing devices into botnets. Spam messages can also be used as part of a tracking scheme to launch future phishing attacks.
6. Man-in-the-Middle Attacks
Since 2016, a mysterious cybercrime group known as the Shadow Brokers has been engaged in stealing and leaking cyber weapons used by the U.S. National Security Agency as well as the Central Intelligence Agency.
The Shadow Brokers are believed to enjoy the support of Russian intelligence services, and have done quite a bit of damage to the American espionage and surveillance apparatus.

By releasing NSA cyber weapons to the public, the Shadow Brokers have made it easy for hackers to perfect man-in-the-middle attacks, which can range from eavesdropping on digital communications to controlling electronic messages. MITM attacks can be as sophisticated as the NSA collecting web traffic by means of posing as Google, but the most common attack involves sniffing data travelling from personal computers to websites and internet apps. If you don’t have a quality home security system, it may be a good time to get one soon.
This particular cyber risk is one of the main reasons more Canadians are taking advantage of some of the most reliable VPN services in Canada (French: Meilleur VPN 2022)
7. The Internet of Things
Smart home devices captured the spotlight during the 2020 Consumer Electronics Show in Las Vegas, but they come with major security caveat: they often ship without adequate security, and this is how they connect to the Internet of Things (IoT). Smart speakers such as Amazon Alexa and Google Home are considered to be major risks because users easily entrust them with information deemed to be very personal.
In 2018, a couple of incidents involved private conversations recorded by the Amazon Alexa speaker and sent to third parties.
The problem with the IoT is that device manufacturers fail to protect consumers for the sake of making the installation process easier. IoT discovery services such as the Shodan search engine have shown just how risky smart home devices can be.
In some cases, web cams can be manipulated so that their digital video output can be streamed to just about any website. In 2024, we should expect to see more IoT privacy intrusions from devices that are not necessarily at home but in our vehicles and even purses.
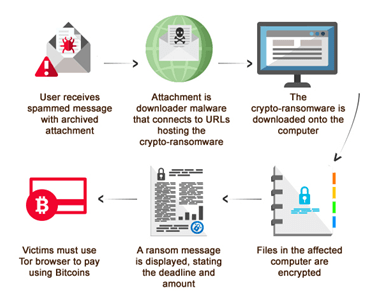
8. Ransomware
This cyber risk brought a good portion of the world to a standstill in 2017 in the form of the WannaCry attack of May 2017.
Not only did this attack manage to infect more than 200,000 computers around the world, it also took down crucial services and mechanisms managed by the National Health Service of the United Kingdom. The headquarters offices of Deutsche Bahn in Germany and Teléfonica in Spain were impacted, and quite a few major companies in Russia were forced to enter a long downtime period.

As its name suggests, ransomware is an attack that makes a ransom demand. The attack mechanism may start off taking advantage of an exploit, In the case of WannaCry, hackers used a cyber warfare weapon developed by the NSA and leaked by the Shadow Brokers.
The second part of the attack consists of encrypting all files within a hard drive partition or stored across network folders. The next step consists of delivering the ransom note, which usually demands payments to be made in major cryptocurrencies such as Bitcoin.
Quite a few ransomware victims have opted to make ransom payments in exchange for a decryption key to unlock their data, however, hackers may also deliver incorrect keys or withhold them completely.
9. Crypto-Jacking Malware
This relatively new cyber risk kept information security researchers quite busy in 2018. Crypto-jacking is a specialized kind of malware coded for the purpose of infecting a system and surreptitiously using its bandwidth as well as its computing resources to mine cryptocurrency.
In 2024, it is expected that crypto-jacking attacks will continue increasing. Hackers are coding crypto-jacking malware in stealthy manners in order to avoid detection by antivirus software, and they are targeting regions of the world by internet protocol (IP) address. So, knowing how to hide your IP address might come in handy.
10. Invisible Malware or Software Subversion
Even though this particular cyber risk may sound like a new threat in 2024, it is actually related to traditional hacking methods. Software is no longer confined to hard drives. It resides in cloud servers and is often delivered as a service, and this method of delivery opens the door for subversion and sabotage.
End users cannot do too much to protect themselves against these attacks because they may not feature files, thus making them virtually invisible. The burden is on the cloud computing providers and software developers to keep their platforms safe and to ensure that they are working with ethical third parties.
See also: How to Fight Common Java Vulnerabilities from DevOps
The Bottom Line
You’ve just read a fairly comprehensive list of the cyber shenanigans online users can expect to encounter over the course of 2024, but there is no way to account for the new and unique penetrations hackers are working on this very moment, which will be released at some point in the near future and perhaps take our fears in an entirely different direction.
There’s not much to do about these yet-to-be-released forms of attack except keep your network and devices completely protected with the latest recommendations from cybersecurity experts. If you’re on a budget, you can check out our list of the best free VPNs. It’s a step in the right direction.
Good luck out there this year!




