Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
How to Fight Java Security Vulnerabilities

Within the last decade, the model for how software development is done has been radically shifted.
Companies are now moving away from hiring dedicated system administrators who manage individual servers.
The cloud computing movement has ushered in a concept known as DevOps.
DevOps is all about collaboration and the term represents a merging of development and operational activities into one role.
Instead of keeping IT and coding tasks in separate buckets and teams, they are merged to produce faster and better results across the entire organization.
The DevOps model gets a lot of praise in the software industry these days, but it is important to be aware of the risks that come along with it. In this article, we’ll look at some of the ways where security vulnerabilities can sneak into DevOps practices and how best to address them.
Practices that Create DevOps Risk

Modern companies stay in a near-constant frenzy to build new websites or expand the content on existing ones, activities often conducted in support of new product or application launches in order to keep up with the competition.
As a result, development teams are expected to write code in an agile manner so that quality assurance teams can run the necessary checks and ship it out the door.
But QA activities often do not have an overlap with cybersecurity best practices, which can leave companies exposed to attack.
Hackers are always looking for new ways to infiltrate IT systems and either steal data or take down infrastructure, usually with a monetary goal in mind. Traditional DevOps groups do not always look at systems from a security mindset, which is why it’s so important to shift to a model known as DevSecOps.
Widening the Attack Surface
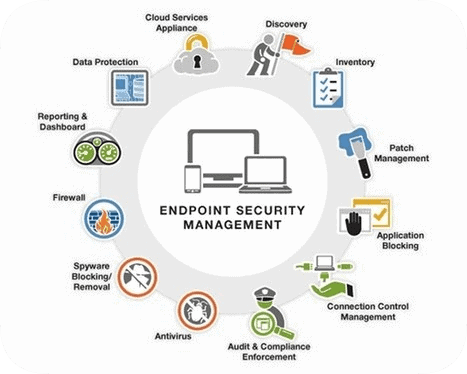
The principles of DevOps are tightly coupled with the microservice architecture strategy, in which all elements of a system are broken into the smallest possible parts in order to increase flexibility.
DevOps engineers then help to empower people across all teams to build products faster and create a flatter organizational structure.
While this type of evolution can lead to huge advancements for a software company, it also widens the range of entry points for cybercriminals. Instead of spending all their energy trying to infiltrate a single endpoint or gateway, hackers can enter the network through a number of different portals.
Security has to be maintained to the same degree across the infrastructure, which many companies struggle to do.
.
Automatic Credential Sharing

In many organizations, DevOps engineers become the bearer of all passwords. Stressing the principle of least privilege is important, as it dictates that employees should only ever be granted the lowest level of access needed to perform their job duties.
But someone in the team needs to maintain administrative control over accounts and services and that tends to fall into the DevOps bucket of responsibilities.
Problems arise when the various authentication and access controls become too complex for one team or individual to manage. This often leads to community passwords and the sharing of authentication or encryption tokens, both of which create risk from a security perspective.
In order to communicate across microservices, software companies will typically employ a container strategy that relies on encryption keys for the transmission of data. However, if the passwords for these keys are stored in a repository as plain-text, it negates all of the encryption efforts and leaves your data vulnerable.
Continuous Integration and Continuous Delivery
As mentioned before, speed to release is often the top priority for new and growing software companies. The best practice in the industry is what’s known as continuous integration and continuous delivery (CI/CD). The goal is to create an agile pipeline that produces flexible products.
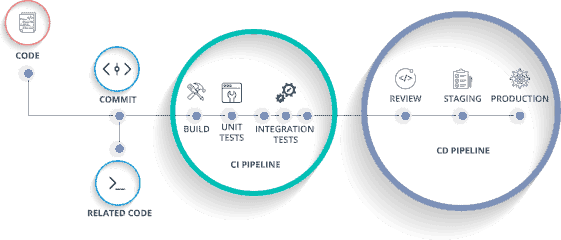
The first piece, continuous integration, urges development teams to check-in small pieces of code changes into a central repository that manages version control. The second element, continuous delivery, is all about pushing those new changes into a testing and production environment in a seamless manner.
But what about security? Unfortunately, when leadership instructs DevOps teams to focus on the speed of CI/CD activities, cybersecurity priorities are usually the first thing forgotten. As a result, there is a higher risk that security vulnerabilities will slip into a codebase, although a fast deployment cycle does allow for them to be patched quickly.
Large Environments with Many Server Instances

The industry-wide move to the cloud allows site owners to create instances in various regions and spread systems and applications across them.
This kind of distributed infrastructure is a competitive advantage for companies built specifically to provide performance-based web hosting services as measured by uptime and loading speed.
The downside is that this advanced hosting environment comes at a price – a higher number of endpoints for hackers to target.
In most organizations, DevOps maintains ownership overcloud configuration and must have clear internal documentation on each instance they operate. Merging into a DevSecOps model will ensure that all servers are handled under a universal security policy that blocks outside threats. The first step is to identify every piece of infrastructure in your organization’s cloud, from automation protocols and cloud storage providers you use down to the fundamental cybersecurity protocols in place to protect your network.
Solutions
Most people make the mistake of thinking of DevOps as a team name or job title. In fact, DevOps is a group of skills, practices, and tools that help engineers build better products. And when it comes to development tools, there are a number of solutions for organizations of all sizes.
Specifically for DevOps specialists, platforms like JetBrains will support modern CI/CD strategies. It allows teams to create code builds directly in a cloud environment and then push into repositories. JetBrains handles all of the complex configuration management needs, so you can easily trace versions of your applications and deploy or rollback when necessary.
Where JetBrains products really prove their value for DevOps teams is with the integration potential. They offer an entire marketplace of plugins and extensions that allow you to connect your systems to third-party products. This means that engineers don’t need to waste time or money building their own internal solutions and can instead leverage tools that connect seamlessly to their existing DevOps framework.