Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
Danger of Public WiFi
When you first hear the words “public WiFi”, it sounds like a good thing. After all, it’s open to the public. That means you get all the benefit without any of the expense!
Not so fast. In fact, you should think of public WiFi like a public toilet. It’s serviceable in an emergency, but it’s best avoided whenever possible. Let’s take a closer look.
What is Public Wifi?

Public WiFi is any WiFi network that’s accessible to the general public. Coffee shops, malls, public transportation, restaurants, and even retail stores often offer free WiFi for customers, or for anyone else who comes along.
This can be convenient for a variety of reasons. You can keep up with social media while you sip your latte, or look up product reviews while you browse a store.
Unfortunately, public WiFi can pose a serious risk to your online privacy. And we’re not just talking about advertisers tracking you. We’re talking about your most intimate, personal information.
For example, suppose you log in to your favorite social media site on a public WiFi network. Someone might get your login information. With that, they can get access to your personal communication, which can give them access to any details you may have shared with friends.
Worse yet, suppose you need to transfer some money from your savings account to your checking account to make a purchase. So you log in to your bank’s app to make the transfer. Imagine what a hacker could do with your online banking password.
Many public WiFi networks require a password for access, which can give you a sense of security. Unfortunately, that sense of security can be misleading. What does all this mean? It means you should avoid public WiFi whenever possible.
Top 10 Dangers of Public WiFi
So, why is public WiFi so dangerous? Here are the top 10 dangers you expose yourself to when you connect to one of these networks.
1. Unencrypted Networks
On an encrypted network, your information is secured by an encryption key. In other words, the information can’t be easily accessed by a third party. When a network is set up by a professional, they’ll typically enable encryption.
Unfortunately, many public WiFi systems aren’t set up by a professional. For example, the router in your local coffee shop is just as likely to have been set up by a barista as an IT pro. And even if the network was set up professionally, there’s no way to tell for sure whether it’s been encrypted.
On an unencrypted network, it’s easy for a third party to intercept your data. Needless to say, this is a serious risk.
2. Phony Hotspots

A phony hotspot is a hotspot that’s designed to look legitimate, but really isn’t. Usually, this is as simple as creating a network with a similar name to the one you want to connect to.
Let’s say you’re enjoying a late lunch at your favorite restaurant. They have a WiFi network called “SouperSalad”. You go to log in, and accidentally select the network called “SuperSalad”. Congratulations. You’ve just connected to a phony hotspot, and hackers are collecting your information.
3. Man-in-the-Middle Attacks
A man-in-the-middle attack is a type of attack where a hacker puts themselves between two devices. When they do this, they’re able to intercept, read, and even alter transmissions.
For example, imagine you’re connecting to a router in an airport terminal. Unbeknownst to you, a hacker inserts themselves between you and the router. So you visit your online trading platform to check on your stock portfolio.
When you log in to your trading platform, the hacker is able to read your username and password. A week later, you log in again, only to find out that all of your money is gone. That’s an extreme scenario, but it illustrates how dangerous this kind of attack can be.
4. Malware Attacks

Hackers don’t always have to read your information while you’re connected to the WiFi network. Instead, they can insert malware into your phone or laptop, which will continue to send your data to criminals until it’s removed. On a public WiFi network, this is particularly easy.
One common method is to create a fake popup asking you to install a software update. When you connect to the network, you see an innocuous-looking notification that your messenger app needs to be updated. When you click it, malware is installed instead.
5. Ad Hoc Connections
An ad hoc connection is a connection directly between two computers. If your device is set to automatically discover new networks, or if ad hoc connections are enabled, hackers can connect directly to your device as soon as you go online.
6. Username and Password Theft
What all of these attack methods have in common is that they expose your website usernames and passwords. This can give hackers access to any online account. They may even sell your login information on the dark web.
7. Identity Theft

Losing control of your username and password can be a problem, but it’s easy to fix. Just change your password as soon as you become aware of the problem.
The bigger risk is the information that cybercriminals can access in the meantime. For example, you might have emailed some tax information to your accountant. If that information includes your Social Security or Canada Pension Plan number, you can become a victim of identity theft.
8. Worms
A worm is a special type of malware. Viruses need to attack a specific program, and generally must be installed. Worms, on the other hand, are able to propagate themselves.
The problem with a public network is that you don’t know who else is connected, and how good they are at protecting their systems. If someone else on the network is infected with a worm, the worm can jump across the network and attack your computer.
9. Snooping and Sniffing
Snooping and sniffing is when a hacker uses software or special WiFi hardware to listen in on WiFi signals. With this technique, hackers can access everything you’re doing online.
The good news about this is that if you’re just reading the news, you aren’t sending any personal information. The bad news is that as soon as you log in to a website, the hackers will have your access to your account.
10. Bitcoin Mining

Bitcoin and other cryptocurrencies require large amounts of processing power for their blockchain encryption. To get this power, they outsource the processing work to other people. As a reward for being part of the encryption scheme, people occasionally receive “free” cryptocurrency.
This process is called Bitcoin mining, and it’s a popular way for people to earn an extra buck. Unfortunately, not all Bitcoin miners are honest people. Sometimes, they use other people’s computers to do the work for them.
What does this have to do with public WiFi? An attacker can use the public network to secretly install Bitcoin mining software on your computer while you’re connected.
Admittedly, this isn’t as serious a problem as identity theft. But because this software uses processor resources, it can significantly slow down your computer.
What Not to Do (If You Have to Connect to Public WiFi)
In today’s world, it’s hard to avoid public WiFi altogether. We’re all addicted to our phones, and sometimes we have to work in the airport or on the train. So, what should you avoid if you have to connect to public WiFi? Here are a couple of pointers.
Don’t Access or Use Sensitive Data
A good rule of thumb when you’re using public WiFi is to assume that your information is being read. Obviously, this isn’t always the case. But as the saying goes, an ounce of prevention is worth a pound of cure.
As a result, there are certain things you shouldn’t access or use on a public network. At all costs, avoid accessing any bank or other financial institution. And never use or send your Social Security or Canadian Pension Plan number on a public network. That’s just begging for trouble.
Many public WiFi platforms will ask you to enter your email or phone number to register for their service. When you’re asked for this information, think twice about whether or not you trust the network. If you decide to proceed, it’s a good idea to use a secondary email address.
Avoid Signing Up For Multiple Platforms
Many public WiFi networks are part of a platform. This is particularly true for chain restaurants, public transportation, airports, and other large venues.
In some cases, signing up for these platforms is inevitable. But try to limit your exposure by signing up for as few as possible. One way to mitigate this risk is by seeing if your internet service provider or phone carrier offers WiFi hotspots in your area.
Avoid Unsecure Websites
Most modern websites use a Secure Socket Layer (SSL) to encrypt traffic. You can tell whether a website is secure because the address will begin with HTTPS instead of HTTP. Snooping traffic on an HTTP connection is much easier than snooping traffic on an HTTPS connection.
On many browsers, it’s easy to tell whether or not a website is secure. For example, Google Chrome will give you a “Not Secure” warning when you connect to a site without an SSL. It’s smart to avoid those sites in general, but especially when you’re connected over public WiFi.
How to Protect Your Info on Public WiFi
Avoiding certain content and limiting the information you share are just part of staying safe on public WiFi. It’s also important to take preventative measures. These measures are also a good idea when you’re connecting to internet at home.
Use a Secure Browser

One good way to protect your information is to use a secure browser. These browsers are fundamentally different from the browsers that come packaged with your device.
Typically, your device will come with a browser like Microsoft Edge, Safari, or Google Chrome. These browsers may seem safe, because they come from reputable sources. The problem is that they’re optimized for speed and ease of use, not security.
Secure browsers include options such as Firefox, Tor, Brave Browser, and the Epic Privacy Browser. These browsers run a bit slower, but they do a better job at keeping cybercriminals away from your personal information.
Use a VPN
Another way to keep your information safe is to use a virtual private network (VPN). A VPN provides a secure, encrypted tunnel between you and the VPN server. Not only does this protect your personal information, but it can help to anonymize your web traffic.
That said, not all VPNs are created equal. For example, there are many so-called “free VPNs”. Unfortunately, many of these services are scams. Instead of hackers stealing your personal information, the VPN service will have access, instead.
That’s why it’s important to stick with a quality, paid VPN service. This will ensure that your information is more secure, not less secure. And don’t leave your phone unprotected, either. There are plenty of good VPN services available for Android and iOS.
Make Sure Your Malware Protection is Up to Date
A good antivirus program can go a long way towards keeping your computer safe from hackers. And if any malware does make it onto your device, regular, automatic scans will quickly identify and eliminate the threat.
That said, even the best malware protection doesn’t do much good if it’s not regularly updated. Always make sure that you’re using the latest version of your antivirus software, and immediately update whenever you see an update notification.
Make Sure Your Firewall is Enabled
When used in tandem with a good antivirus program, a firewall can prevent many types of online attacks. A firewall is a barrier that protects from many types of attacks, including any unauthorized traffic or unwanted connections. When a firewall detects any suspicious data packets, they will be blocked.
Sometimes, using a firewall can be annoying. They can prevent some programs from working, and they give frequent popups and notifications. As a result, many people turn their firewalls off while they’re at home.
If you normally keep your firewall off, turn it on before connecting to a public WiFi network. In Windows, you can do this from the System and Security section of your Control Panel. Mac users can do this through the Security & Privacy section of the System Preferences.
Turn off File Sharing and AirDrop
If you work in a collaborative environment, you may use Windows File Sharing or Apple AirDrop. These services allow for anyone to easily put files onto your device. In the workplace or the university, this is a useful feature. However, on a public WiFi network, this same feature can pose a serious risk.
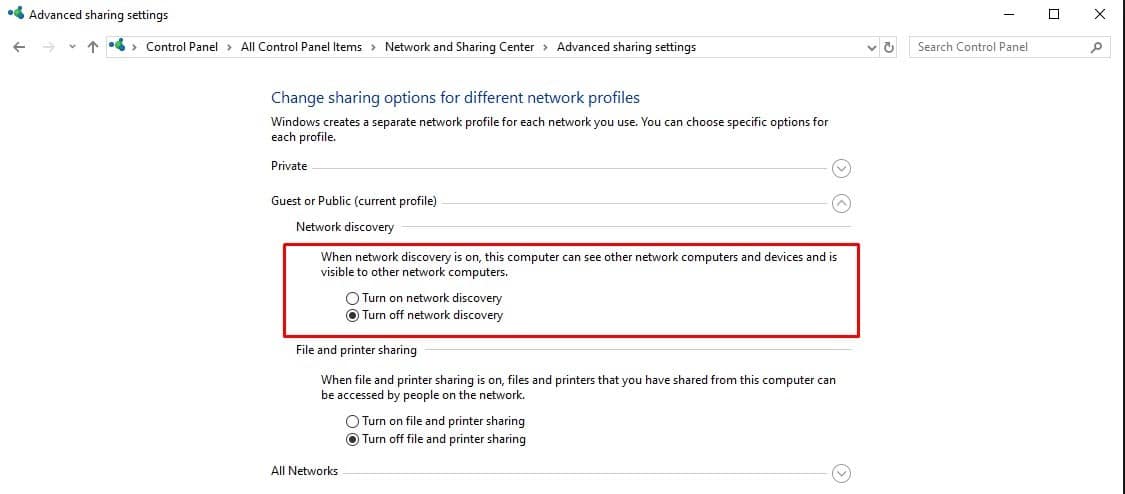
Windows users can disable file sharing by going to the “Network” portion of the Control Panel, clicking on the Sharing Center, navigating to Advanced Sharing Settings, and turning off file and printer sharing. For Mac users, open the Finder, click on AirDrop, and select “Allow me to be discovered by: No One.”
Changing these settings won’t provide 100% secure connections. But it will ensure that no-one can simply drag and drop malicious files onto your hard drive





