Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
Online Privacy: 11 Ways To Protect Yourself in 2024 (and Beyond)
Saying “online privacy” often sounds like an oxymoron given the opposing nature of those two words. It is similar to trying to argue the possible existence of a cold fire or hot ice. In translation, it stands for something counterintuitive and improbable.
In 2024, however, there are very few things as important as being cautious about one’s data on the internet. Those who are mindless about their privacy can even find themselves in a position of stolen identity, fraudulent charges, or worse.
In a sense, overlooking one’s anonymity is similar to getting inside of a car after cutting the brake lines and putting a jet engine under the hood. Meaning, it is bound to result in a disaster of grand proportions.
Luckily, the world has just as many caring individuals as it does hackers. Thus, people have found many ways to protect their online safety by applying some fairly simple techniques.
In order to avoid joining the group of 16.7 million individuals whose identities were stolen in 2017, everyone should adhere to the following pieces of advice.
1. Hide Your Phone Number
Sharing one’s mobile phone number online presents a careless mistake that hinders privacy.
First, it allows a potential hacker to pinpoint one’s location through nothing more than a simple look-up of the area code. Luckily, however, obtaining a phone number does not give a malicious user too much leverage.
So, the real danger of posting phone numbers online comes from telemarketers. These are the people or robots that place calls from randomly generated numbers that may match one’s area code.
Then, once the user picks up, they attempt to sell some product or gather more of their data. Unfortunately, these calls will be nearly impossible to opt-out of once somebody’s phone number has been compromised.
Given how widespread this problem is, the Federal Trade Commission created various “Do Not Call” registries. Thus, a way to improve privacy after making a mistake of oversharing a phone number is to sign up on these lists.
Sometimes, doing so will eliminate the problem. Then again, it could just simply put a brief stop to the constant calls until the telemarketers’ notorious persistence prevails.
2. Be Careful on Social Media
As of 2018, there are 2.34 billion users on social media websites. First, this means that everyone’s aunt and uncle have a profile and frequently overshare family pictures. Second, it means that hackers have a perfect way to locate potential victims.

Being present on social media is very risky as it often includes personal photos, location insights, spending patterns, browsing histories, and much more.
If a hacker is able to get their hands on any of these data points individually, it could be a disaster. So, the fact that they can reach all of them together in one place practically sets up a field where one is giving away all relevant information on a silver platter.
Sometimes, hackers even pretend to be someone else and attempt to meet with you to get information from you personally. It is recommended to get a good home security system to ensure complete protection from these scenarios.
In order to increase privacy, the most reasonable thing to do is to stay away from social media platforms. That, however, is not the easiest alternative as many people use these websites for family interaction, business communication, and much more.
So, the next best choice is to avoid posting personal photos, keep all profiles private, never share any location information, and rarely or never purchase things directly on these platforms.
3. Block Location Services
A lot of popular internet service providers (and most major websites) track and store your location for data-gathering purposes. Then, they sell this information to companies that can use the locations to customize their marketing campaigns and properly target individuals.
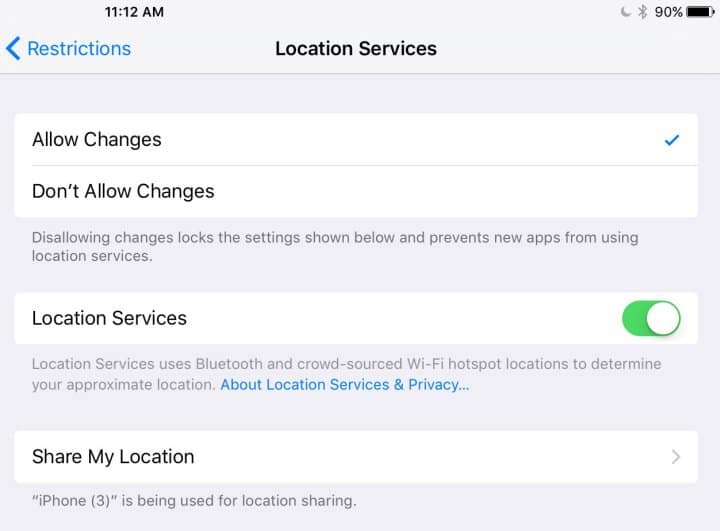
As amazing as it may seem in theory, seeing other people’s locations through online maps is not too popular in real life. After all, imagine tracking down a person through online location check-ins just to greet them. The likely outcome of this scenario would be a phone call to 911.
Therefore, turning all location services off and never allowing websites to have access to them is crucial. For instance, there is absolutely no need to allow an iPhone game to track one’s location.
Regardless, most apps will ask the user to share this data with them.
4. Choose Your Browser Wisely
When it comes to online browsers, users have quite a few different options. The most popular ones tend to be Google Chrome and Mozilla Firefox. Also, Apple’s Safari could be labeled as successful since the company practically pushes its users to take advantage of it.
Contrary to popular belief, none of the aforementioned platforms offer high-grade privacy. Even some incognito-based searches are not fail-proof and will not completely mask one’s data. Instead, using custom-made browsers that were specifically optimized for privacy is the best course of action.
These tend to be open-source programs that are encrypted and offer absolutely no insight into one’s online activities to anyone. Some of the most common choices include:
- Tor
- Brave
- Epic
- Firefox Quantum
Additionally, taking advantage of plugins like “HTTPS Everywhere” minimizes the odds of online hacking and data theft.
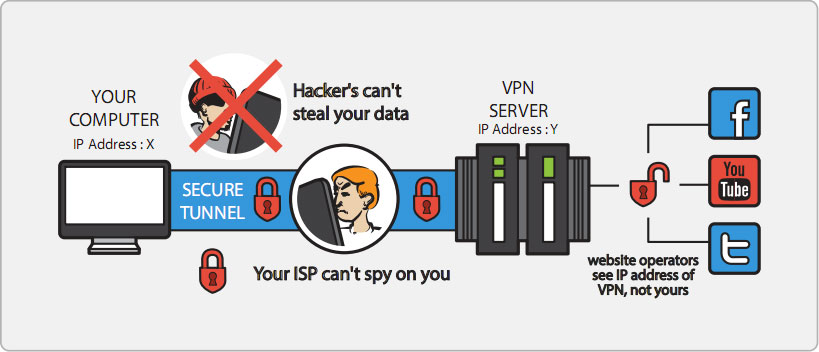
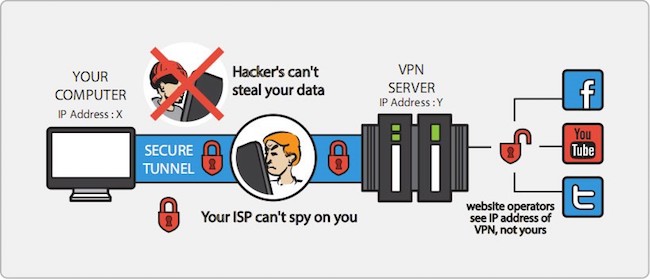
5. Use A (Secure) VPN
Virtual Private Networks are used to turn computers that are connected to public networks into devices that communicate via private connections. They work by routing an internet connection through servers that hide all of the user’s actions and online data.
Besides increased privacy, the best VPN services allow users to sometimes overcome issues related to geographical restrictions. (If you speak French, check out Meilleur VPN).
For example, there are many websites that will avoid displaying content to people who are located in specific areas. Think about all the YouTube videos that are not shown to people registered in certain locations.
Also, a large part of why VPNs are so powerful stems from their ability to anonymize people’s online actions. Meaning, entire browsing histories can become non-existent as most records of someone’s actions on the internet through VPNs are not kept.
Not to mention how these networks are capable of completely hiding one’s IP address.
Related: Best Cheap VPN
6. What about e-mails?
Upon mention of online privacy, most individuals tend to think about actual websites that people have to go online for. In reality, however, there are many ways that a person’s privacy on the internet can be compromised. One of those ways relates to e-mails.
Obviously, the most important concern about e-mails goes back to user’s data. In order to sign up for an account with almost any platform, one will usually have to provide their full name, date of birth, address, and even phone number. All of this data is potentially subject to theft if a hacker decides to attack someone’s e-mail.
To avoid issues of this nature, people should try to use false information when signing up for e-mails.
For instance, creating a different, generic name with a made-up address is the easiest way to stay off the grid. In addition, there are no laws preventing people from making e-mail accounts as they see fit.
Additionally, it is imperative never to use one’s e-mail lightly. In translation, signing up for random newsletters, databases, or other campaigns is the shortest route to junk mail with potential phishing scams.
For those unfamiliar, phishing scams are made to trick users into entering their information on web pages that seem identical to what they are used to.
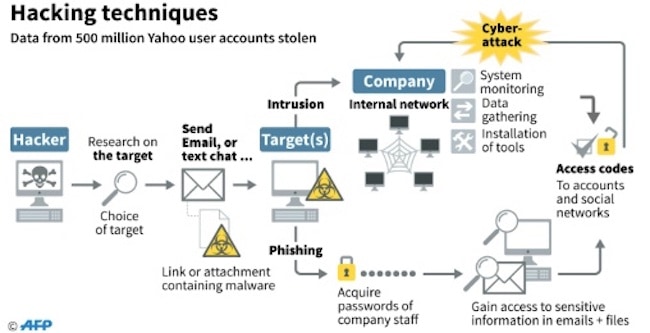
7. Two-Factor Authentication
For users that are present on popular websites like Facebook, Apple, YouTube, Yahoo, Google, or any others, using two-factor authentication should not even be a question.
The easiest way to explain how it works is to look at a simple process of getting into one’s account on any of the aforementioned websites.
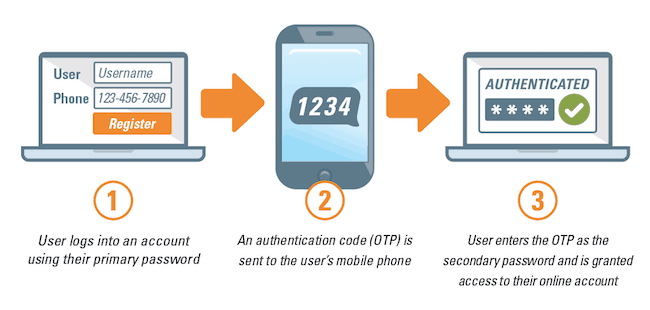
In the past, websites generally required users to enter their username or e-mail accompanied by a password. If those two matched, they would be taken to the platform and allowed to continue browsing.
With two-factor authentication, there is an additional step that adds a third device into the equation. Besides the username and password, people will also have to enter a second-level code that will be sent to their e-mail or phone. Then, the website will ask for the code which they sent after the user enters the original username and password.
The reason why two-factor authentication is necessary comes from its superior privacy benefits. It ensures that whoever is attempting to sign in somewhere is also the one that has access to other points of contact like a phone number or an e-mail that was previously registered with the account.
Since the odds of some hacker also having access to the victim’s private e-mail account or telephone messages are low, it is very unlikely that they will get through the two-level authorization.
Related Read: 2FA Guide
8. Guard Your Passwords With Your Life
The times when people could use “password” for their password are long gone. Nowadays, phrases need to look more like something that the Pentagon may use to access their own systems. Although this is an evolving trend that keeps putting more requirements in place every year, it is the easiest way to disallow fraudulent activities.
Luckily, the vast majority of websites and apps already require users to create complex passwords that contain lower and upper-case letters, numbers, and even special characters. Nevertheless, if one runs into a platform where there are no specific rules on password creation, they should still make them as complex as can be.
Many online users take advantage of password managers to generate, keep track, or even recover complex word-based seeds. The most popular ones include Dashlane, 1Password, and KeePass.

Moreover, one of the most misrepresented pieces of information deals with the safety of fingerprint scanning. After certain phone companies implemented seamless ways to log in by tapping a button that scans one’s finger, the vast majority of users started relying on this feature.
Unfortunately, extensive research indicates that these scanners can be tricked through online hacking that creates prints from various human features. If that was to happen, the hacker could effortlessly bypass every single password somebody has as long as they were also using their fingerprint to log in.
8. Heed the Warnings!
At times, one’s computer or phone may give a warning stating how the connection may not be private and the danger of other people seeing someone’s sensitive data exists. Shockingly, an incredibly high number of people tend to ignore these messages.
The rationale behind this is their belief that no sensitive information can be stolen if the user is not displaying any such data at the moment. The issue with that claim, however, is the fact that hackers can take data which may be months or years old.
Thus, someone’s credit card information from two years ago could be located through previous payment methods that are almost always saved somewhere. Therefore, a piece of essential advice for those who want to adhere to an ultimate privacy guide is to exit any compromised website, WiFi, or any other connection.
9. Consider Using Cryptocurrency
This step is probably meant for people who might have done all of the previous steps and are looking for more advanced ways to protect their assets. Well, courtesy of cryptocurrency, investors can now purchase things anonymously.
To start using cryptocurrency, one first has to purchase their digital coins with real money. Electronic trading allows people to do this very fast. Once they obtain their currencies, they must store them on one of the online wallets or trading platforms.
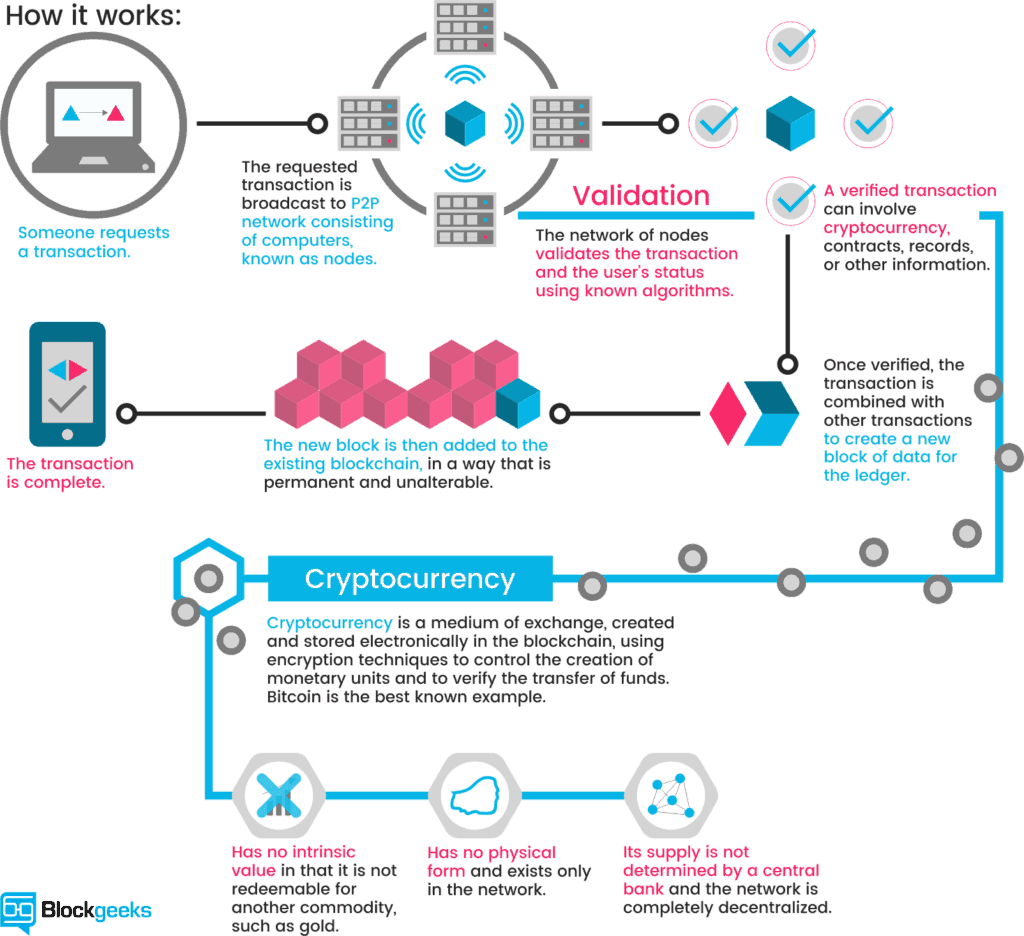
Lastly, the person has to use their cryptocurrency for paying whenever possible. The only shortcoming is the fact that a lot of platforms have yet to adopt crypto-based payments. Once they do, however, everyone should consider these coins instead of debit or credit cards.
10. Monitor Your Bank Accounts and Credit Scores
Sometimes, the most shocking part about the identity or data theft is how long it took somebody to find out.
This remaining hidden is because hackers may harvest people’s data until they find the right buyer. Once that happens, the buyer may spend more time waiting for the perfect chance to use another party’s information.
In some cases, people may not even be aware of multiple loans that exist in their name.
Well, this can be easily fixed by regularly checking all bank accounts as well as obtaining a copy of the credit report at least twice a year. The reason why people can rely on credit agencies is due to their close monitoring of everyone’s finances.
After all, credit scores are calculated based on someone’s spending habits, outstanding debt, consistency in monthly payments, and so on. Meaning, if there is identity theft and the attacker uses another person’s name to open new lines of credit, this should showcase on the victim’s credit report.
11. Log Out!
The last step that facilitates better privacy goes back to the basics. It merely advises everyone to always log out of their accounts. Doing so means logging out from every app on their phone and all programs on their computers, especially when traveling.
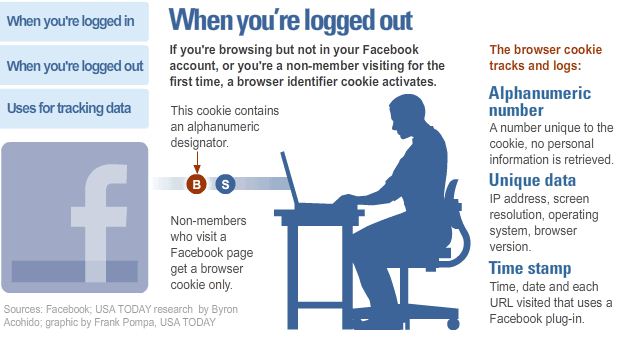
Although it may seem excessive, taking this action will save one’s information if they get their hardware stolen. For example, a stolen phone where all accounts are already available will be much easier for a hacker to break into.
To go even further, leaving accounts logged in creates a potential danger to all others who may be associated with the irresponsible party. Think about the private conversation that people may have on Facebook, per se. In case a device goes missing, the entire content of those conversations could become public knowledge.
For the ones guilty of this, a simple act of logging out will exponentially reduce the risk of stolen information or any negative consequences.
Privacy Evolves
There are many more relevant tips for those who want to improve their online privacy. However, taking a look at some of the safest VPN providers, such as NordVPN and Surfshark, is probably the most important step. Sadly, many of these pieces of advice could become irrelevant soon.
This often happens as privacy laws change and the technology gets better.
For instance, the entire issue revolving around human fingerprint scanners on mobile devices did not even exist until a few years ago. Similarly, robot-based telemarketers and scam-like phone calls did not take off until the early 2010s.
So, knowing what recent changes related to privacy have occurred would be useful when it comes to preserving identities, financial data, or other information. It would also make one much less likely to succumb to common myths or be neglectful of their online safety! On the other hand, we also made a comprehensive guide on E-Safety for anyone interested in doing whatever it takes to protect themselves.