Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
Full Guide to Unblocking Websites
As we will discuss, governments are concerned about their image. At the same time, those in power want to protect their power. So how do they strike the balance? They do so by playing with semantics. How so? The terms filtering, shut down, blocking, and censorship means the same thing from the point of view of the end-user.
Basically, the idea is that there’s some part of the Internet that you cannot access. However, to governments, policymakers, and activists each term carries a different connotation. The term “filtering” seems gentle and mild. In reality, the term “censorship” seems more Orwellian in nature as you will soon find out in this article.
Throughout this guide, we will use the four terms intermixed. But for the sake of this guide, they all mean the same thing—a part of the Internet cannot be accessed.
Governments Want to Keep their Glory
The list of countries that ban websites is a who’s who list of authoritative regimes. Prominent on these lists feature names like North Korea, Yemen, Turkey, and Iran.
While the majority of the world enjoys unrestricted access to the Internet, including the use of social media sites like Facebook and Twitter, the above-mentioned countries are so concerned that their citizens might say something negative about the government that they prevent them from using social media and visiting other sites that the government deems dangerous.
These governments are suspicious of their citizens. Something as simple as using a GPG signature for advanced encryption is seen as a threat to the state.
Unblocking Websites – #1 Solution, Get a VPN
Simply put, a VPN creates a connection between your electronic device, be it your computer, tablet, or smartphone, to another computer in a different part of the world known as a server. This encrypted connection allows you to surf the Internet while your IP address is hidden, using the VPN server’s IP address as a mask. So, if you are in China, but you are connected to a VPN in London, it appears as if you are in London. This gives you access to content that you would not usually be able to access.
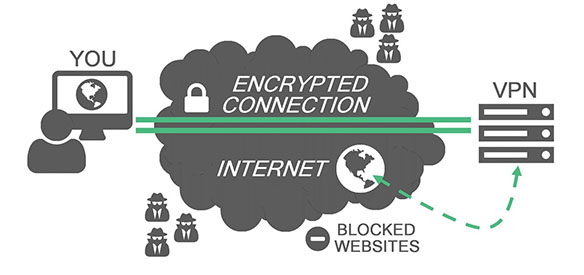
There are a number of VPNs on the market. Many of them offer their services for free. Some free VPNs can be dangerous because they either lack proper encryption and good VPN protocols, or they are used as a tool to gather your personal information and then sell it to marketers. Remember, the encrypted connection, or the secure tunnel that allows you to pretend like you are in a different part of the world, is also the same VPN tunnel that all of your Internet traffic is going through. If the VPN that you use is not trustworthy, they could do whatever they want with your private information.
We have reviewed countless VPNs and have selected two that we feel are hands down the best of the bunch. They are NordVPN and ExpressVPN.
Our Number One Pick: NordVPN
NordVPN is our top recommendation. This VPN gives you access to more than 5,200 servers around the world. You have the ability to connect six devices simultaneously. NordVPN offers additional features, including leak protection as well as obfuscation to get around software designed to block VPNs.
Their specialized servers, including double VPN servers and tor-over VPN servers, improve your anonymity and make getting around geo-blocking a snap.
Pros
- Double hop VPN servers
- Live chat support
- 30 day money back guarantee
- Provides access to geo-blocked streaming services like Netflix
- User-friendly
Cons
- Connection speed sometimes fluctuate
Pricing
NordVPN is a touch more expensive than some of the other paid VPNs. However, they offer a considerable amount of value for what you get.
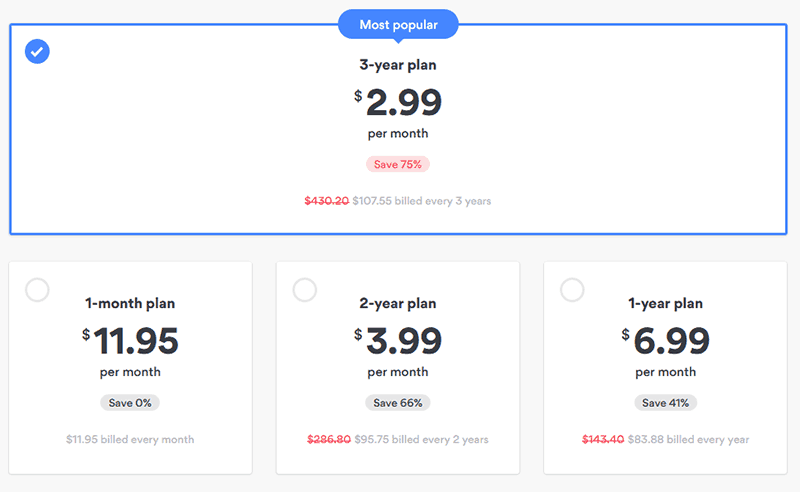
- On a month by month basis, you will pay $11.95.
- If you pay for one year at a time, you will pay $83.88 a year, the equivalent of $6.99 per month.
- If you pay for two years at a time, you will pay $95.75, the equivalent of $3.99 per month.
- Their most popular plan is a three-year plan. You pay $107.55. This breaks down to $2.99 per month for three years.
All of their plans come with a 30 day money back guarantee. You can pay using credit cards, cryptocurrencies, as well as other forms of payment.
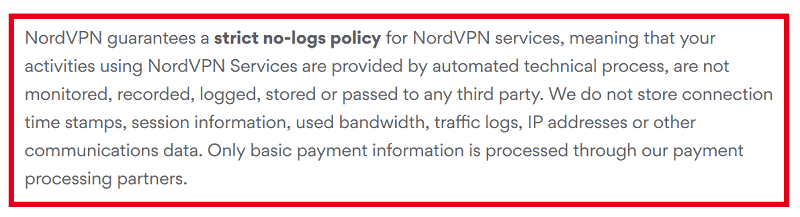
Logging Policy
NordVPN is one of the few VPN services that has been verified to have absolutely no logs. They have been audited by accounting firms that verify their no logs policy. They do not store IP addresses, Internet activity, or traffic logs.
We strongly feel that NordVPN is the best VPN service for getting around geo restriction blocks and other techniques used by governments to prevent people from accessing the Internet. Check out our full NordVPN review.
Our Number Two Pick: ExpressVPN
ExpressVPN is based in the British Virgin Islands. As such, it is protected by the privacy laws designed to cover businesses and individuals operating there. This means your privacy is protected. ExpressVPN has more than 3,000 VPN servers. They offer their clients 160 VPN server locations spread across 94 countries.
A short while ago, ExpressVPN updated their apps for all of their platforms. The result was improved connection speeds, improved reliability, and a better layout.
Pros
- Fastest VPN service that offers superior encryption
- Secure connection
- Works in China
- A large number of servers and server locations
- Allows P2P
Cons
- Expensive
- Three device limit
Pricing
Price is a big factor to watch out for when choosing a VPN, ExpressVPN markets itself as a premium service and as a result, is offering their services for a lot more compared to another premium service like NordVPN.
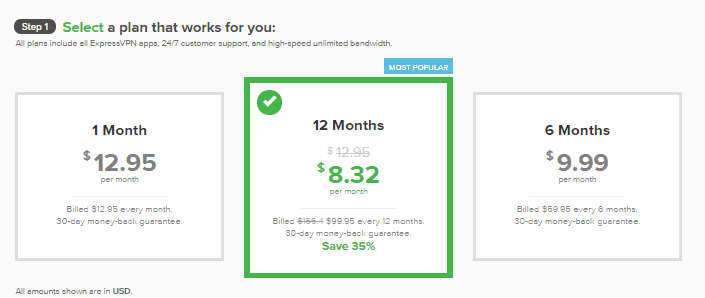
- $12.95 per month if you pay per month
- $8.32 per month billed at $99.95 per year
- $9.99 per month with a six month contract billed $59.95 every six months
ExpressVPN allows you to pay with credit card, PayPal, cryptocurrency, as well as a host of other forms of payment.

All of their plans come with a 30-day money back guarantee.
Logging Policy
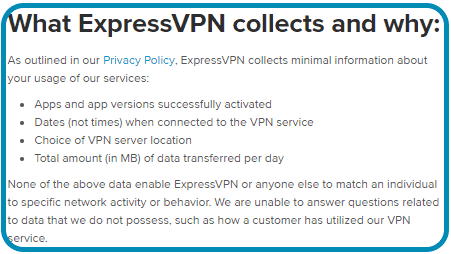
Time and time again, ExpressVPN has proven itself trustworthy when it comes to keeping customer’s privacy. As such, their VPN logging policy is one that is often sought after by many people looking to get released from the eyes of the goverment.
One of the better-known examples took place in December 2017. Authorities in Turkey seized ExpressVPN’s servers. They wanted to get customer data. Authorities were not able to obtain any customer data from ExpressVPN’s servers because they had no logs.
ExpressVPN will not store:
- Browsing history
- DNS queries
- Traffic destination
- Metadata
- IP addresses
If for some reason NordVPN does not work for what you want, ExpressVPN is a quality service that has proven itself to be trustworthy. We give them our full recommendation. Check out our full ExpressVPN review.
Other Ways to Unblock Websites
Although a VPN is the most effective solution, it may not be for everyone. Here are some other ways to unblock websites (All of the solutions here may work, but they all fall out on a few major things that a VPN service provides).
Using Proxies
A proxy is going to work a lot like a VPN in that it will give the appearance that you are surfing the web from a different location. What proxy servers do not offer is encryption. So while you may get around geo-blocking, there is no guarantee that your traffic is safe from prying eyes. In fact, the site most likely knows that you are using a web proxy, specially if you are using one without encryption.
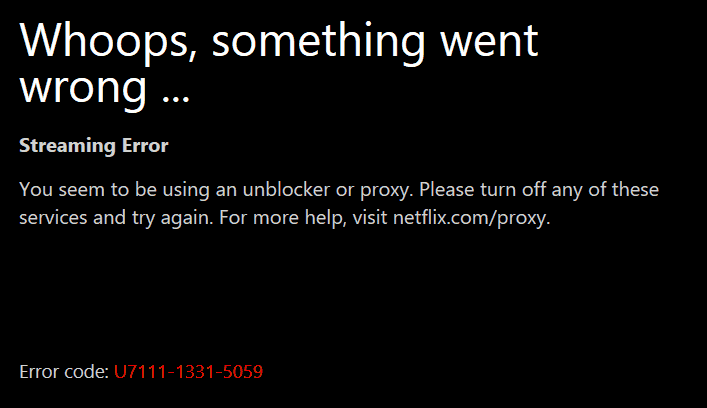
Take for instance, Netflix. They have developed a system to block your access to their streaming service when their system detect that you’re using a proxy to bypass restrictions. This is when the dreaded Netflix proxy error shows up:
This is another case of why proxies can’t really always solve the problem. For a few websites only filled with text information, proxies could work. But in the case of streaming sites like Netflix, it is best to use a VPN to gain access to them.
Replacing Your DNS Server
If you’re using Open DNS, you may be able to bypass attempts to filter out certain websites. To do this, use of following instructions:
- Go to Control Panel
- Find Network and Sharing Center
- Click the name of the Network Connection you are using
- When the next window pops up, click Properties

- Highlight Internet Protocol Version 4 TCP/IPV4
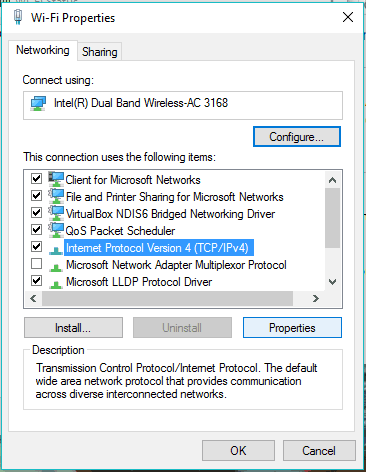
- Select Use the Following DNS Address preferred DNS 208.67.222.222 alternate DNS 208.67.220.220
Since the use of Internet Protocol Version 6 – IPv6 is becoming more popular, you may want to make the same changes there. Perform all the same steps as before, but highlight the Internet Protocol Version 6 and click properties.
Change your Computer’s DNS server addresses:
- Preferred DNS server: 2620:0:ccc::2
- Alternate DNS server: 2620:0:ccd::2
There are a number of reasons why governments prevent their citizens from having free access to the Internet. The following are the four most popular.
Why Do Governments Censor Websites?
There are many reasons why governments censor content on the internet. Often, these reasons are summarized by saying: “to preserve the state of national interest“. Essentially, it’s a way for these powers to remain in control, keep the local population ignorant and prevent any revolution from starting with a single idea (After all, everything big starts with a single idea). It’s a state of mind where the only God that you know is a 5-inch 5-foot fat man who talks a big game but leads a country using hunger and fear as the driver.
Of course, not all nations operate this way. While their reasons may be different, in the end, it still inhibits a nation’s freedom of speech and freedom of opinions. Take a few minutes to go through the main reasons why censorship still occurs in the 21st century,
Afraid of Revolution
The “Arab Spring” that started in northern Africa and spread through much of the Arab world was able to grow as quickly as it did thanks to the Internet.
When repressive governments see these types of things happening, they become afraid. They realize that unhappy citizens can use the Internet to quickly organize riots and mobs. So these governments will block social media networks, hoping to prevent people from communicating with each other during times of unrest.
Protecting a Country’s Image
All countries are concerned about their image. They guard their image better than the best home security system guards the home of a rich man. They recognize that their image impacts the way they are treated by other nations. Even countries that are now thought of as beacons of freedom, like the United States, tried to control their image during times of unrest, such as during the civil rights movement. Image-conscious countries today like China and North Korea strictly control Internet use as a way of protecting their reputations and hiding the reality of internal conflicts.
Politicians Want to Keep Power
Regardless of the country, incumbent politicians want to stay in power. Recently, in Benin, the Internet was severely throttled in what many felt was an attempt by the incumbent power to rig the elections.
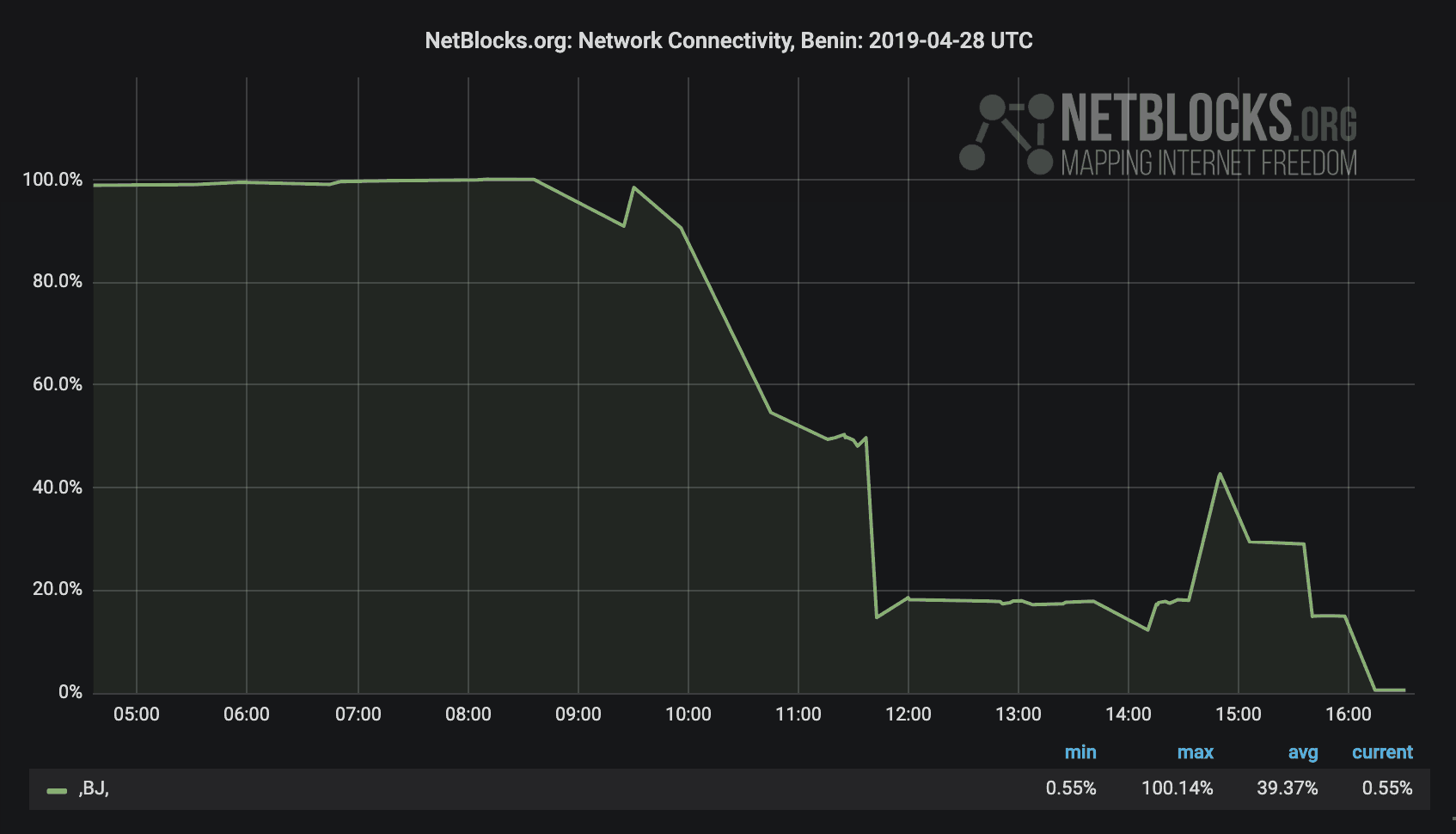
In many cases, this is done with the goal of preventing minority groups from organizing counter movements or preventing minority groups from showing evidence of brutality aimed at preventing them from voting.
Grounds of Morality
A number of countries around the world block websites that the government deems to be immoral. For example, just a few years ago, India ordered their ISP to block more than 850 adult websites with the goal of protecting moral decency. On the same grounds of morality, India tried to ban social media sites Facebook and Twitter because they felt that the sites refused to take down offensive content.
What Are the Tools That Governments Use to Block Websites
There are a number of tools and tricks that governments use in order to “protect” their citizens from dangerous sites. Let’s take a look at a few of them.
The Great Firewall of China
There are approximately 800 million people in China who are online today. These individuals are unable to access YouTube, Facebook, the New York Times, or Google. If they try to investigate the 1989 protest in Tiananmen Square, events are presented in a way that is favorable to the government. Believe it or not, there was even a time when Winnie the Pooh was not able to get around the Great Firewall of China.
The Great Firewall of China is an effort between government monitors and telecommunication companies designed to enforce the state’s rules. Because of its success at banning the Internet, China has become a model for repressive governments around the world.
The Golden Shield Project is a database surveillance system that allows China to record the Internet actions of each one of its citizens. The government employs 50,000+ people whose sole job is to bar websites the government disapproves of and filter out content that the government deems harmful.
China controls all eight of the ISPs in the country. They also control the 10 international Internet gateways that connect China to the rest of the world.
IP Blocking
A favorite tool of the Chinese government is IP blocking. This is an easy technique to implement. Routers in China are given a list of undesirable IP addresses. Routers will drop any packet that is going to one of the blocked IPs. This way, users cannot establish a connection. The downside of this, aside from the obvious censorship issues, is that there could be other websites that have the same IP address that will get blocked if it is on the same server.
Keyword Filtering
If IP blocking is relatively easy to implement, keyword filtering is sophisticated. It uses an Intrusion Detection System, inspecting all traffic that goes through the ISPs that handle China’s incoming and outgoing traffic. If the traffic has a predefined keyword that is blocked, then the traffic is suppressed and the TCP connection is reset. The reset happens on both endpoints, which force a connection to close. Then the connection is blocked for up to one hour.
The Great Firewall of China is constantly evolving. There are probably a number of tricks and techniques that China is using to censor the Internet that are not known to the public at large. What we do know for a fact is that many of China’s methods have been borrowed by other countries, which have adopted these techniques to suit their own purposes.
Brazil Bans WhatsApp
In 2015, WhatsApp did not give the Brazilian government data that it wanted about an investigation it was doing. So the Brazilian government responded by banning WhatsApp’s IP address. The court ordered the blackout for 48 hours. The effect was immediately felt since over 90 percent of the country’s population uses the messaging service. It is especially popular among poor individuals who can’t afford to pay the ridiculous fees for phone services.
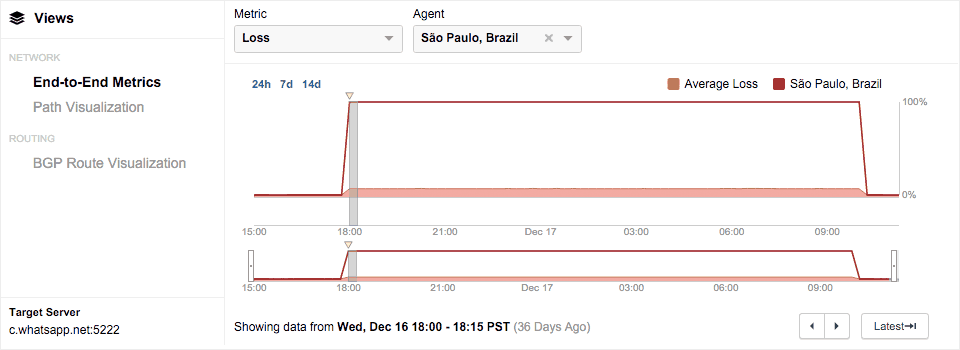
How did the Brazilian government accomplish this feat? Well, when you look at the Internet traffic, you see that all packets are lost for one node that has a private IP address of 10.223.238.77. With a simple IP block, the Brazilian government was able to get the routers armed with an IP backlist to drop all of the packets going to WhatsApp’s IP addresses.
Pakistan Creates an Internet Black Hole
There are two primary ways of censoring the Internet. You can emulate what Brazil did and configure the access control list to drop all the packets from a blacklisted IP. Or you can divert the traffic that’s going to the forbidden site to a black hole location by creating a more specific route that literally points to nowhere.
This is what Pakistan did. In February 2008, Pakistan was upset with YouTube because it did not take down what they felt were anti-Islamic videos. So Pakistan created a /24 routing table for YouTube. What this means is that instead of advertising its usual route of 208.65.152.0/22 in Pakistan, it was advertising the route 208.65.152.0/24. This is a little bit more of a specific prefix than the one that YouTube usually uses. So all Internet traffic that was supposedly directed toward YouTube in Pakistan got directed to nowhere.
Unfortunately, the/24 routing advertisement was leaked by mistake to an ISP that is in Hong Kong. Since the prefect announcement was not validated, the ISP in Hong Kong saw it as a preferred route and began spreading the information to its neighbors. In short order, two thirds of the Internet around the world was affected by this leaked routing table for YouTube’s IP.
The Tools Governments Use to Block the Internet
There are five common tools that governments use to block the Internet. Each one of these tools has distinctive features that control how they operate. The five tools are:
- IP and protocol based blocking
- Deep packet inspection based blocking
- Platform based blocking
- URL based blocking
- DNS based blocking
IP and Protocol Based Blocking
As we discussed with the Great Firewall of China, IP based blocking blocks all of the traffic to a set group of IP addresses. With protocol based blocking, low-level network identifiers, such as TCP/IP port numbers, will be used. Really, this type of blocking doesn’t block content, but it blocks IP addresses. This can be done by installing software on a computer. In many cases, it’s done for network security.
Another option is to throttle the traffic from a particular IP. If the government opts to do this, they are not completely blocking the traffic. They are going to make the speed of it go up and down. The goal is to get users so frustrated or to make the service seem so unreliable that the user walks away.
Whether we are talking about IP blocking or protocol-based blocking, the device that does the blocking is in between the user and the content. For this reason, the entity that is doing the blocking needs to have complete control of the Internet connection between the source and the Internet user. Users who use the best VPNs, a technology designed to conceal the true destination of Internet traffic, would not be affected by this form of blocking.
Deep Packet Inspection Based Blocking
This is a more comprehensive form of blocking. There are devices between the end-user and the Internet that filter the content based on a set of criteria, including application types, the type of content, or certain patterns. This is an expensive form of blocking because all of the content that comes in has to be compared to the blocking rules of the DPI.
In order for DPI blocking to work, there has to be some signature information about the content available. It could be traffic characteristics, including transmission rates or packet sizes. It could also be keywords, file names, or the information that is specific to the content that one wants to block.
This makes DPI blocking an effective way of pinpointing certain types of content as long as the content can be identified using signatures. An example of this would be blocking all VoIP traffic. DPI blocking does not work as well when the goal is to block a particular file or documents that have particular keywords.
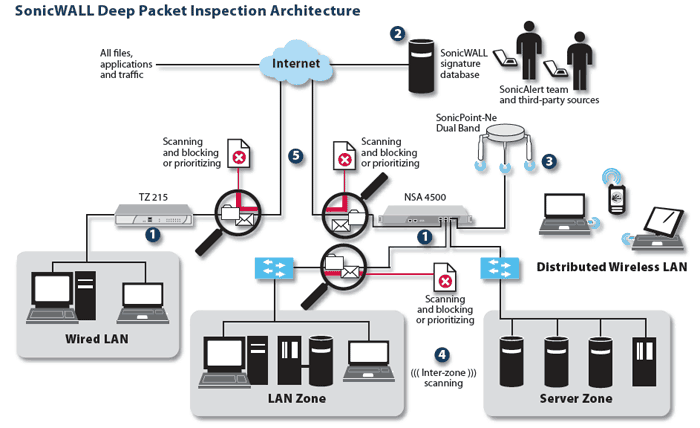
Also, DPI blocking is invasive because it requires examining all of the traffic that is sent to an end-user. Deep packet inspection blocking has worked well in countries like China when the goal is management and security enforcement. It does not work as well when the end goal is to create policy based blocking.
URL Based Blocking
A popular way of censoring the Internet is URL based blocking. This blocking can happen on an individual computer or can be set up in on network devices between the computer and the Internet. URL based blocking works with web-based applications. However, non-web-based applications, such as VoIP, are not affected by this form of blocking. With this process, a filter is put in place to intercept HTTP traffic. The URL of said traffic is then checked against a database that is stored locally or a service that’s online. Depending on the response, the filter will either block the connection or allow it.
When URL based blocking is used, the user is either completely blocked from visiting the banned site, or the user is redirected to a site that has a warning or a policy statement emphasizing why said site was blocked. In order for URL blocking to work, the ISP or the party that is responsible for the blocking needs to have the ability to control and intercept the traffic that travels between the end-user and the Internet.
Platform-Based Blocking
This form of blocking will require that the platform owner and the entity that is requesting the blocking, in this case the government, work hand-in-hand. When an individual sends out a query and they live in a country where certain websites are banned, they will receive a different set of results as compared to the rest of the Internet. Content that is considered objectionable will be blocked.
Search engine blocking is only going to impact people who use said search engine and who are living in a geo location where the filter rules apply. It’s important to understand that this type of blocking does not filter out the content. It just filters out the pointers to the content. In other words, Google is not going to direct people to pages that are deemed inappropriate by the government, but all a person needs to do is switch their search engine or use other methods of finding content to gain access to the prohibited materials (Read more: Best private search engines)
DNS Based Content Blocking
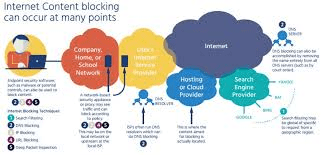
DNS content blocking is designed to control and examine DNS queries. The DNS resolver has two primary goals. The first is to perform DNS look ups. The second is to compare names against a blocked list. Imagine that a computer attempts to use a blocked name. After examining the computer’s DNS address, the server is going to return information that’s incorrect
It might redirect someone to an IP address that displays a notice saying that certain content has been blocked. Or the server might tell the computer that the content does not exist. Whatever the technique used, the effect is the same. The user is impeded from gaining access to content that the government feels is dangerous.
FAQs
Q: How do I unblock site at work?
A: Your employer is understandably concerned about safety and how their employees make use of their time. Part of providing good security is seeing to it that employees use the best password manager. Part of seeing to it that employees make good use of their time may be blocking certain websites that are deemed time wasters or dangerous. However, if you have a valid reason for wanting to get around the restrictions your employer has put in place, we recommend that you use a VPN. VPNs like NordVPN and ExpressVPN will allow you to get around blocked sites.
Q: How do I permanently block a website?
A: If you want to do this on your computer, you can set up a block at the operating system level. This is not difficult to do, and it will work for both average browsers and secure browsers.
- To do this, you will need to have administrator access to your computer. Then go to C:WindowsSystem32driversetc
- Find and double-click the file named “Host”
- Next, open Notepad. You are going to see the last two lines on your host file read: # 127.0.0.1 localhost” and “# ::1 localhost At the end of the file with 12 7.0.0.1 add the name of the site you want block. For example, if you want to block Google, you would do 12 7.0.0.1 www.Google.com. Repeat this step until you have added all of the sites you want to block.
- Close the host file, click Save, and restart your computer.
Q: Can schools block VPNs?
A: Yes they can. One of the most common ways is for system administrators to close ports that are most commonly used by VPN tunneling protocols.
Q: Does my internet provider know what sites I visit?
A: Yes. They absolutely do. Your ISP serves as the mediator between you and the Internet. Unless you are using a VPN like NordVPN and ExpressVPN, which not only make your traffic anonymous but also encrypts it, everything that you do can be monitored by your ISP.
Final Thoughts
Really, there are a number of ways to try to get around geo-blocked content. Some of them require little bit more work than others, and some of them are little bit more consistent when it comes to the results that they produce. For our money, the best way to unblock websites is to use VPNs, like NordVPN or ExpressVPN. Both of these products have a stellar track record when it comes to removing restrictions on the internet imposed by the government, a school, or other institution.
We would love to hear from you. Tell us about the tools that you use to successfully unblock sites. Let us know in the comments section below. Also, check out our FAQs section for more information.






