Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
VPN Logging Policies: Who Captures What Data?
One of the main reasons why you need to invest in a great Virtual Private Network service is to avoid documenting activity in a way that others can see or manipulate it. Most VPN services emphasize their dedication to transparency and protecting your data during transmission and not retaining records after the fact.
That sounds great and all, but did you know that logging policies can widely vary?
Always Marketing a Zero-Log Policy
It’s not unusual for VPN services to point out better privacy due to lack of logging. The thing is, that statement is usually true to some extent, although, the qualification may be found in the small print. For example, it’s likely true that the service in question does not log data unless it’s required by the governmental laws that apply in the country where the service is based.
You must remember that just like any business, VPN service providers always put their best foot forward.
You must remain vigilant.
Which Logs Are Kept?
There are three primary types of logs that a VPN service is likely to maintain, at least, only for a short period of time. In fact, the providers often state specifically which one, or how many of the three types they will retain.
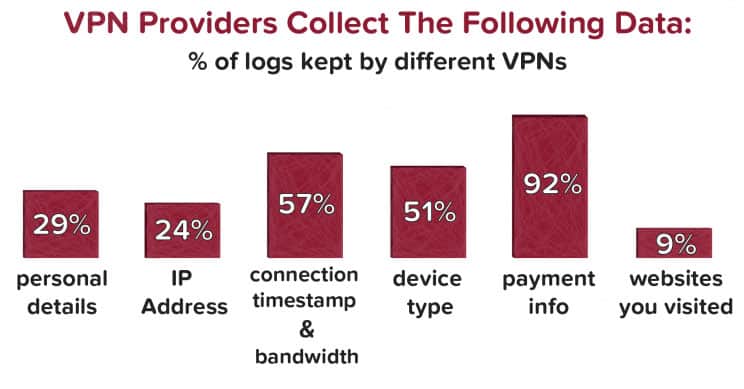
Most VPN’s erase logs within 30 days. However, this isn’t always the case and it may change depending on the company. So you must find out which logs are kept, and then find out how long they keep the data.
Listed below are the types of logs that are typically kept by a VPN service provider:
- Activity Logs: this is a record of all traffic that comes through the VPN network. Depending on how the logs are structured, it may or may not be easy to track back specific shared files or other data to a specific user.
- Connection Logs: Services that place limits on how long a connection can remain active do keep these logs, as well as how many connections are active for a specific client. This makes it easier to manage the connections and terminate one or more if necessary
- Error Logs: These track back to connection or performance issues with the network proper. Information about customers affected by the error may include logging the IP address and/or the username of the client.
Learning Who Logs What

In order to know what sort of logging policies apply, it’s absolutely critical that you read the terms and conditions associated with your account thoroughly. You will always have the chance to review all of those provisions before you sign up for the services.
Unfortunately, many people make assumptions about logging and other policies, and do little more than skim the terms and conditions before creating an account. That can lead to some unfortunate situations later on.
Keep in mind that VPN service policies may be slightly structured differently to remain compliant to local laws. In that case, you may find that focusing your search for the top provider of VPN services is influenced by where the company is based from.
Anonymizer
You may have heard of the Five Eyes. This refers to five nations that have entered into an agreement related to online security. Those five countries are Australia, Canada, New Zealand, the United Kingdom, and the United States.
Anonymizer is hosted in the USA, meaning that the provisions agreed upon by the Five Eyes impacts their logging policies. All types of logs that are considered legal to capture under the terms of that agreement are maintained for a specified period of time.
The idea behind the logging is to allow the data to be shared with national authorities in the event some sort of national security breach is suspected. How long the data remains logged will depend on the current laws that apply.
Anonymizer is up front about this only to a certain extent. If you read their terms and conditions, you will find clauses that affirm the logging and more information about why it takes place. Their sales and marketing collaterals are less clear about what is and is not logged, so be sure to still do your due diligence.
Astrill
Astrill is unique among the services found on this list, in that it’s located in Liechtenstein, a microstate located in the Alps between Switzerland and Austria. They have a strict no-logs policy where no personally identifiable information is kept. No logs are stored on their VPN servers once the connection is terminated.
During active sessions, their system does keep track of connection time, IP addresses, device type, total number of transferred bytes, and the version of the Astrill VPN application being used. This information helps them ensure proper technical functioning of the services as well as determining if they should plan network expansions. However, no personally identifiable information is kept.
The last 20 connection records which are stripped of personally identifiable information are kept and used only by their customer support team to provide support on potential VPN connection issues. That information is automatically removed when there is no activity for 30 days and you can also request manual deletion of it by contacting their support team.
Buffered
Buffered is based in Gibraltar and chooses to maintain their servers in that country. While Gibraltar is considered a British Overseas Territory, it’s generally considered to not be bound by the regulations found in the Five Eyes agreement.
That means the odds of having information shared with security agencies in other nations is slim at best.
In their privacy policy as well as their advertising, Buffered affirms that they do not monitor download or browsing activity. In fact, they do not claim to maintain any type of activity logs.
The service does maintain some connection logs, retaining information like the on and off times for each connection, the duration of the connection, and the amount of data that is transmitted and received. Incoming IP addresses are also included in the connection log. The data is maintained for no more than 30 calendar days.
CyberGhost
CyberGhost hosts servers in Romania. Since the nation does not have any detailed reciprocity agreements about Internet data with other nations, there is very little chance that your activity will be shared with agencies or other parties outside the country.
Like many other services based in nations with no agreements to share data with others, CyberGhost does not maintain activity logs.
Error logs are maintained as a way to track and identify trends related to network issues.
In like manner, connection logs are maintained as a way to evaluate peak periods of server activity and prevent overloads. Both types of logs are kept anonymous and are not used for any purpose other than protecting the integrity and function of the network.
ExpressVPN
ExpressVPN maintains servers in the British Virgin Isles. Like Buffered, the information sharing that takes place among the countries involved with the Five Eyes agreement does not extend to this location. That means your online activity is highly unlikely to be shared with any foreign entity.
The connection logs maintained by ExpressVPN are considered bare-bones when compared to a number of other VPN services. That data includes which of their servers were used and the date that each session started and ended. Unlike some other services, the client’s IP address is not captured for the connection log.
Unlike some of the other services on this list. ExpressVPN does not track your activity. They don’t even monitor your account’s bandwidth usage. They prefer to operate by monitoring overall usage on the network and use that data to determine when there’s the need for more servers or some sort of network upgrade.
HideMyAss
HideMyAss is based in the United Kingdom. As one of the nations who participate in the Five Eyes agreement, you can expect some of your data to be logged.
In the event some sort of investigation into a possible national security breach occurs in any of those five nations, your data could be shared as part.
You do get some idea of what type of data is logged. For example, the privacy section of the terms and conditions state that HideMyAss will not log data about the websites you visit while connected to the VPN.
This means there’s a limit on what appears in the activity logs. The connection logs are more detailed and include information like your originating IP address, how long each session lasted along with the start and end times, and how much bandwidth was used during each session.
Hotspot Shield
If you prefer to utilize a VPN service that has no agreements to share online activity with other nations, Hotspot Shield is a good choice. Based in Switzerland, there are no legal provisions for sharing any type of Internet activity. That means anything you do while connected to the VPN is highly unlikely to be shared with any other source.
For internal purposes, Hotspot Shield does generate connection logs for each session. One thing that’s a little different is that the log is erased at the end of each session.
The company also does track browsing activity although it’s not clear to what degree that activity is tied back to individual users or even to users authorized by a specific customer. The activity log does not include IP addresses, but customers should know that their browsing and other activity is still tracked.
IPVanish
IPVanish maintains servers in the United States. The company does observe the terms and conditions found in the Five Eyes agreement. As a result, there is the possibility of your activity being shared with law enforcement and security agencies based in other nations.
That being said, IPVanish operates with a zero-logs policy. That means they do not actively maintain activity, connection, or error logs.
Data can be captured while a session is in progress, but it appears to be deleted from the network once the session ends.
IPVanish is a firm believer in the right to online privacy. That has led the company to aggressively support the Electronic Frontier Foundation and its efforts to ensure privacy for all Internet users.
Goose VPN
With servers in the Netherlands, Goose VPN operates in a nation that has established security alliances with several other nations. The result is that your activity could be shared in the event of some sort of international investigation.
The activity logs maintained by the service omit any type of personal information. However, the connection logs do capture data like the type of operating system used by the individual device and the physical location of the user.
Even though IP addresses are not included in the connection log, the other data could be helpful in terms of identifying specific users.
NordVPN
The servers for NordVPN are based in Panama, a country that has no specific agreements to share customer activity with agencies based in other nations. The result is that your activity is highly unlikely to be shared with anyone.
According to the NordVPN’s privacy policy, there are no activity, connection, or error logs maintained for any amount of time. Basic information associated with your account, such as your name, email address, and your IP address are maintained, but are not shared with any entity outside the company.
Private Internet Access
Another VPN service that’s based in the United States, access to your activity is subject to the terms and conditions found in the Five Eyes agreement. There is some chance that your information could be shared with security agencies in any of the participating nations.
The Private Internet Access‘ privacy terms are not as precise as some of the other services on this list. There’s a statement that the company does not capture any type of VPN traffic logs at all.
On the surface, this suggests that the service does have an actual zero-log policy, and that no activity, connection, or error logs are available for sharing.
StrongVPN
StrongVPN also hosts servers in the United States, ensuring that the company seeks to comply with the provisions found in the Five Eyes agreement.
In the event of an international incident that appears to compromise security, your data could be requested and shared.
The company does not maintain activity, connection, or error logs on any of their servers.
Data is used in real-time fashion to investigate any reports of connection issues, but is not kept for purposes of reporting to outside entities. If requested by security agencies, basic data about your account might be shared.
TorGuard
The presence of TorGuard’s servers in the USA could mean that customer activity could be shared with agencies in any of the nations who participate in the Five Eyes agreement. At present, the company does maintain a no-logs policy, so any data shared would not include history about your account’s connection times, bandwidth usage, file sharing, or anything other than basic account information.
VyprVPN
As the second service on this list based in Switzerland, VyprVPN is under no obligation to share your connection, activity, or error log data with any other entity. In fact, the company does not record any user activity, up to and including downloads.
VyprVPN does maintain connection logs. The logs include details like session start and end times, the amount of data transmitted during each session, and the originating IP address for that data.
ZoogVPN
While based in a self-governing British Crown dependency, ZoogVPN is not subject to the terms found in the Five Eyes agreement. As a result, the odds of your activity while logged into the VPN being shared with any agency is low.
At present, ZoogVPN states that the company operates with a zero-log policy. While activity logs are not maintained, there does appear to be some data related to bandwidth usage maintained on their servers.
Final Thoughts
Which service provides you with the level of privacy that you need? Only you can be the judge. Whether this is your first time investing in a VPN or you are a seasoned pro, research your options carefully.
Use the information found here as a starting point. Investigate any service that you are interested in to see if they are really the best VPN. With time and effort, you will find the VPN provider that meets all of your conditions for quality, performance, network stability, and privacy.