Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
How To Setup and Use the TOR Browser
Between intrusive government regulations, record-breaking hacks, and growing concerns about the erosion of privacy, many are looking for ways to protect themselves and their businesses from unnecessary intrusion.

For years, those who need to maintain anonymity on the net have used The Onion Router (TOR) network and browser. However, the average internet user has only ever heard of this network as a shadowy platform that allows users to access the dark side of the web, where hackers and criminals lurk around every corner. But is that really all there is to it?
The purpose of this guide to using TOR is to provide an overview of what it truly is, how it works, and why a platform like this is necessary. If you’re concerned about data privacy and internet safety, this is a good place to start.
I’ll be your TOR guide, so let’s go.
What is The Onion Router?
Before you can get anything out of our guide to using TOR, it’s important to understand what it is and what it does. TOR is an acronym for The Onion Router project, so named because it sends IP requests through layers of encrypted relay servers.
It’s both a non-profit network and a browser, and it’s built using the same open-source protocol as Mozilla Firefox. It might be considered a more secure, customized version of the popular web browser.
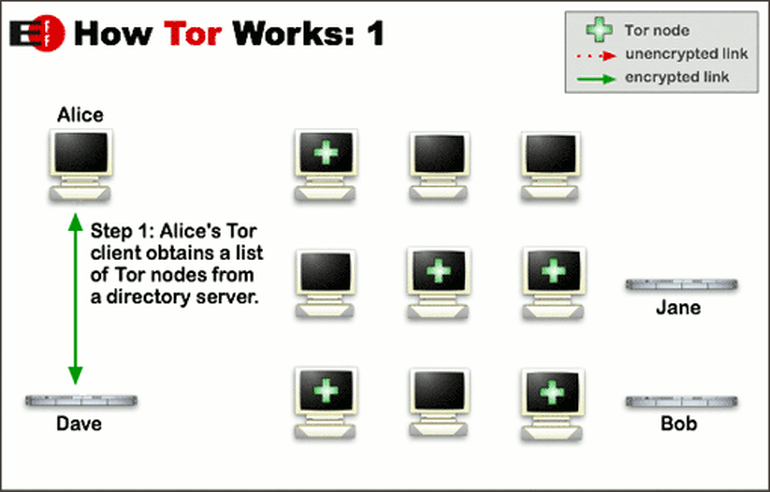
Although the technology used to power this network has been around for a while, the protocol was developed at the US Naval Research Laboratory in the mid-90s; the network was launched in 2004. It’s currently used by approximately 1.5 million people around the world.
There are two parts to the project, the browser software and the network, which is operated by volunteers and organizations from computers scattered across the globe. The more people who are involved in this transmission of relays, the faster and better the network performs. That’s good, because one thing the network is known for its sluggish performance as the traffic sheds layers.
This system of computers is known as relays, nodes, or routers, and they work together to pass requests from user IP addresses anonymously through a SOCKS interface. SOCKS is an internet protocol that exchanges packets between the client and server using a proxy server or series of servers.
The exit relays, aka exit nodes, are the ones that come under scrutiny when an individual user does something illegal or offensive. Some of these relays are publicly listed, but some are not. Those are known as bridges, and they’re used to get around government censorship in oppressive countries like China.
The open source technology is utilized in a way that protects users from deep packet analysis that could be used to determine IP addresses, gain access to information stored in tracking cookies, find out the physical location of computers, or even see and record cursor and mouse movements while you’re using the internet. It does this by providing a secure browsing tunnel once you log on to the network.
However, there are some problems using the network and/or browser, which the tech community is working hard to get around. One problem is that TOR blocks some Firefox plugins and add-ons by default to bolster security.
Then, there are cases where the server blocks TCP/IP proxying via the SOCKS interface, or prohibits DNS proxying by software that supports SOCKS. One enterprising developer created a security tool called Tortilla to help move all TCP/IP and DNS traffic through the interface without interference.
Is The Onion Router Network Right for Me?
Urban legends aside, TOR is a tool. Like many useful tools, the network and browser can be used for good or evil. While there’s certainly a lot of nefarious activity and shady characters populating deeper layers of the internet, many good people need anonymity too.

The Network is commonly used by:
- Political dissidents living under oppressive regimes
- Journalists and investigators
- Law enforcement task forces tracking drug or child/sex trafficking rings
- People living in countries where web access is restricted or censored
- People working overseas who want to mask their location or home IP address
- Anyone else who’s concerned about digital tracking and surveillance
If you’re concerned about your privacy and safety in the real world, you should protect your identity in the cyber world by using The Onion Router’s network.
Navigating the Dark Web Safely
Contrary to popular belief, using this network doesn’t make people more prone to illegal activity. Criminals are going to criminal with or without additional privacy while they rob and wreak havoc. Use some of the same precautions that you would use any time you’re visiting a less-than-safe area, and you should be okay.
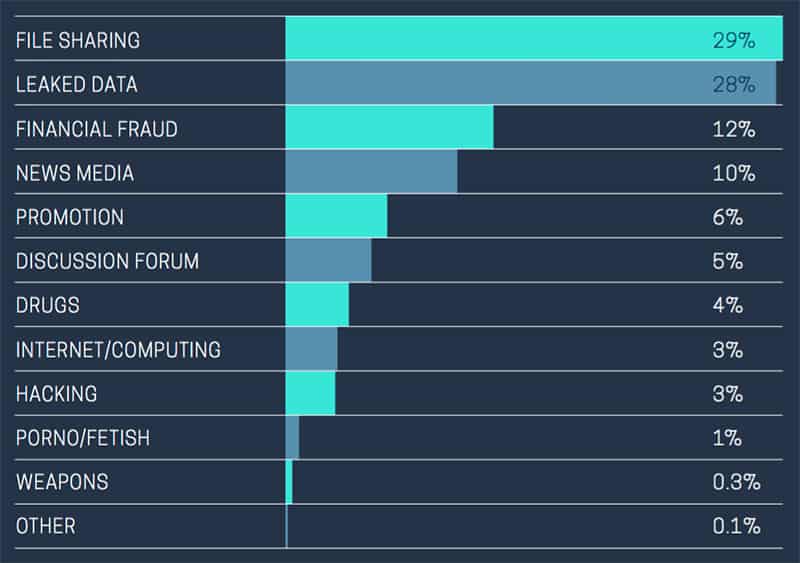
Most common purpose why people use TOR
Due to abuses, many internet service providers use a TOR exit node block to ban IPs that have racked up abuse complaints. Sometimes, just the fact that you’re using TOR is enough to garner unwanted scrutiny or complaints.
You can avoid exit node issues and other problems by following a few proactive tips.
Keep to the Dark Web during your surfing session:
It’s much easier to avoid a TOR exit node block if you steer clear of them. Jumping back and forth between the darknet and clear net means entering and leaving the encrypted tunnel, causing you to encounter multiple exit nodes.
The more nodes you exit from, the greater the chances of hitting a bad one. Essentially, only browse from one at a time. Don’t have a Google Chrome open and a TOR Browser open at the same time.
Make sure the websites you visit use HTTPS
The network uses this more secure protocol by default when it’s supported by the websites you’re visiting. Make sure that the alert light is green before transmitting any potentially sensitive data.
Use services that retain your privacy
The Onion Router protects your anonymity, but it isn’t foolproof. You can enhance your security and privacy by using a search engine that doesn’t track your searches or activity, by adding one of my top-recommended VPN services to your configuration, and by securing chats with a secured messaging platform like Wire.
Furthermore, using Tor will make you safe from common non-criminal privacy invasions, such as browser fingerprinting.
Avoid logins/profiles
Try to steer clear of websites that require you to create an account or a profile, even if it’s free. Every time you do anything on the internet that requires you to provide information about yourself, you run the risk of it landing in the wrong hands.
Should You Beware of the Dark Web?
No guide to using TOR would be complete without some mention of the Darkweb, its Hidden Wiki, and Urban Legends. This is the portion of the internet that most people are fascinated with – and a bit afraid of – when they think about the hidden parts of the internet.
The term “dark web” is often used synonymously with “deep web,” but they’re two separate portions of the same thing.
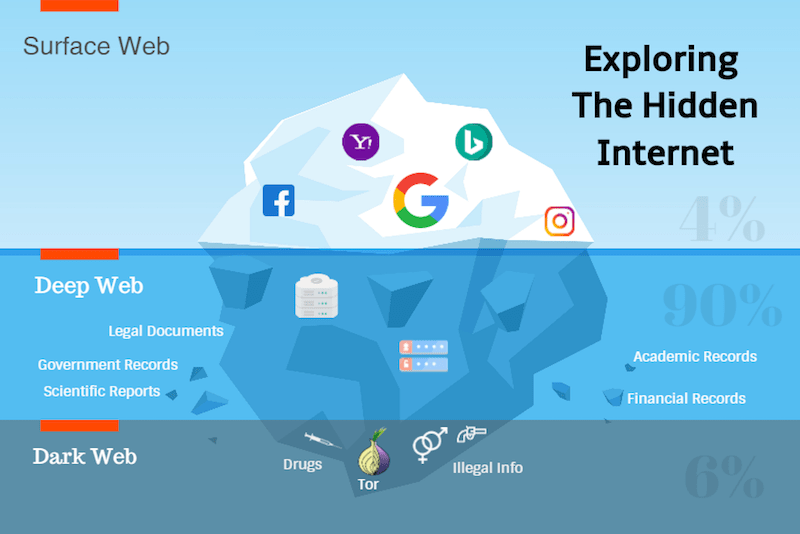
The internet is basically divided into three parts, the clearnet (where most people congregate), the deep web, and the dark web. It’s sort of like an iceberg, with the tip – clear net – visible above the surface, and the rest hidden below. The deeper you get, the darker the waters. You’ll be able to recognize websites located on the Deep or Dark web by the suffix .onion on their URL.
Browsing the seamy side of the internet can satisfy curiosity for those who like lurid details and urban myths, and it can be used for illegal activity. You can also surf the dark web to find out if your information has been compromised or business hacked; it’s used by private investigators, intelligence agencies, and local LEOs, too.
There are also a lot of legit services and interesting places available on the dark web, like the Hidden Wiki (Note: can only be accessed by browsing through The Onion Network). The Hidden Wiki is a directory of websites and services around the deep web. Some are useful, but many links lead to dark and dangerous places.
Just for fun, check out:
- Deep web Facebook: Enjoy the good things about Facebook with a little more anonymity. It has more than one million daily visitors, but you’ll need the NoScript plugin to enable JavaScript to use it.
- NotEvil: This is the deep web version of Google, also known as “the Anti-Google”.
- Proton Mail: A secure email service developed at CERN
- Deep Web Radio: Stream digital radio that caters to any musical taste.
- Strongbox: Super-secure, Wikileaks-style file sharing service run by the New Yorker
- OnionWallet: Secure, deep web-based Bitcoin escrow and payment platform
Be forewarned that if you use the network to stalk or harass people, your IP could trigger an exit node block and get it – and you – kicked off the server. Acting recklessly or criminally may also bring you to the attention of law enforcement agents, who also lurk the deep/dark web anonymously. This can happen even if you’re just minding your own business.
Some companies offer security services for those who need to access this part of the internet or are concerned about personal or business information that might be leaked and appear on Dark Web sites.
An example of a company that doesn’t directly offer these services, but does have this dark web checking feature is Dashlane, which is one of the best password managers out there. Specialized security companies can help with strategy and risk management or locate stolen information like credit card numbers, social security numbers, and intellectual property.
You may find the services of these companies useful:
- Tripwire: Provides monitoring and security services
- Surfwatch Labs: Tracks intellectual property and provides cybersecurity strategy planning assistance
- Hold Security: Provides Deep Web monitoring assistance
- Massive: Performs threat mitigation analysis
- ID Agent: Provides threat alert service
You can avoid problems by following a few common-sense rules while using the deeper net:
- Go with purpose; don’t get distracted and fall down a rabbit hole
- Finish your business, log off, and disconnect from the network
- Never reveal your identity or information to someone you interact within the Deep/Dark web
- If someone seems sketchy or suspicious, avoid further contact
- Protect your identity and location further by using the network in combination with the best VPN
- Never stream video, engage in P2P file sharing, or enable plugins while surfing on the deep web
TOR-Over-VPN or VPN-Over-TOR: Is There a Difference?
Common sense would tell you that the more security and privacy platforms you use, the safer you and your data will be. The Onion Router can be combined with a VPN service, but which configuration is best? Is there a difference if you install one first, and which one?
The first thing you should do is find out if your VPN is compatible with the network or shop for a VPN that is. Then, you can decide how best to combine them.
Both have advantages and disadvantages. As with most tech decisions, your ultimate choice depends on what you’re trying to achieve.
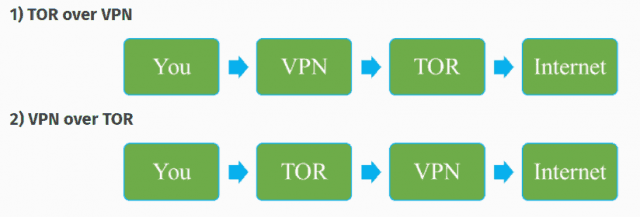
TOR-over-VPN requires you to connect your VPN before logging on to the network. This will encrypt your session before you venture into the darker side of the internet, and keep your ISP from learning that you’re using The Onion Network.
It’s also easier to combine the two with little-to-no tech knowledge, and it’s the more secure configuration. The downside is that, while it masks your IP address upon entry, it exposes it when exiting a node.
On the other hand, VPN-over-TOR encrypts your data after you enter the network. This offers the advantage of disguising the fact that you’re using a VPN. It will also mask your IP as you exit the final node.
However, it will tell the internet service provider that you’re using an alternative browser. It also prohibits you from accessing the network’s hidden services. If you’re trying to hide your session, be aware that this configuration creates a fixed end-point and enables de-anonymization.
Installation Guide and Tips

Installing The Onion Router on your computer or mobile device is really no more difficult than installing any other software or app. Except for iOS-powered devices, the installation process involves only minor adjustments from OS to OS.
Installation for Windows
- Go to https://2019.www.torproject.org/download/download-easy.html.en
- Click the link to download the browser for Windows
- Choose your OS version and preferred language
- Click “Save” and destination folder
- When the download is complete and the box pops up, choose “Run” and follow installation instructions
- After installation completes, click “finish” and open the browser to start browsing
Installing TOR for MAC Users (manual installation)
- Install either Homebrew or Macports package manager
- Install TOR using either brew install tor with the configuration /usr/local/etc/tor/torrc (Homebrew) or sudo port install tor with the configuration opt/local/etc/tor/torrc (Macports) in the appropriate terminal window
Automated Download for MAC Users
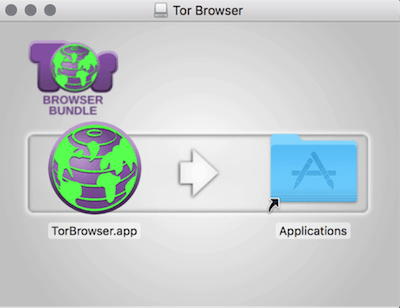
![tor installation for mac]()
- One automatic download completes, navigate to the destination folder
- Find the file TorBrowser.dmg
- Double click this file
- Find and drag the TorBrowser.app to your application folder
- Eject the TORBrowser icon from the sidebar to unmount it
- For first use, click Launchpad and double click browser to open it
- Configure the app according to instructions
- One it’s configured, click “Connect” to launch
Installation on Linux Systems
- Go to the download page
- Choose GNU/Linus download and language
- When download completes, find and extract installation file
- Choose destination directory file, and click “install”
- Follow instructions to open and launch browser
Installation for Android-Powered Devices
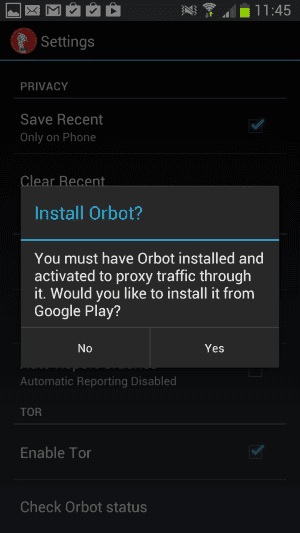
The TOR-supported browser for Android smartphones and tablets is called Orbot. It’s free and available at the Google Play store. Use it in conjunction with ChatSecure for truly private browsing and chatting on the go on Android and iOS-powered devices. There is a global option and an option to use it in VPN mode.
- Go to the Google Play store
- Type Orbot into the search bar; it will reveal a link for “Orbot proxy with TOR”
- Click the link
- Click the “Install” button
- Once the download completes, click the “Open” button
- Follow the instructions to setup and use your browser
- If you choose to run it in VPN mode, a key icon will appear at the top of your phone screen when it’s active.
Using TOR With iOS-Powered Devices
With iOS devices, you’ll need to use a third=party app called the Onion Browser that’s available at the apple App Store.
- Go to Apple App Store and search for Onion Browser for iOS
- Click “Install”
- Launch Onion Browser app
- Click “Connect to TOR”
- Once launch has initialized, wait for message that initialized is completed
- Browse as usual
Common Sense Steps for Privacy Protection
Although browsing with TOR provides a high level of anonymity, it isn’t the end-all or be-all of online privacy. As soon as you check your email or perform other routines tasks, your privacy may be compromised.
The answer to stopping data leaks and breaches is to follow privacy protection best practices like constructing hard-to-crack passwords and other common-sense mechanisms.
In addition to the privacy offered by this browser, there are several other ways to protect you and your information online. For example, DuckDuckGo is an encrypted search engine that offers a private, secure alternative to Google. You can search the internet, including the deep web, without being tracked and profiled.
Another security measure is The Amnesiac Incognito Live System (TAILS). This live Linux distribution platform that was popularized by Edward Snowden.
Rather than installing it on your computer or mobile device, the TAILS OS lives on a USB thumb drive. This prevents any user of the dark or deep web from being traced to a specific computer or being caught in by the NSA search engine, XKeyscore.
Is TOR Alone Enough?
This platform offers a way to surf the internet and reach places that can’t be reached via commercial browsers and traditional ISPs. However, it doesn’t cover your tracks completely. Email is one of the biggest threats to your online privacy, and any time you look at your inbox, you’re unmasking yourself.
If you run a commercial website, you should also make sure that you use the most current security protocols like secure socket layers (SSL), transport layer security (TLS), and military-grade 256-bit AES encryption standards. Business owners and individuals should also sign up with a good virtual private network like NordVPN. This will ensure end-to-end encryption on all of your networks and connected devices.
Tor FAQs
We’ve tried to make this TOR guide as comprehensive and easy to follow as possible, but some of you may just want some quick answers to your burning questions. Here are a few of the most common.
Q: Is it illegal to access the Deep Web?
A: This is probably one of the questions most people who’ve heard of the area known as the Deep Web ask. The Deep Web is simply a collection of unindexed web content and IP addresses that need different protocols to access. This includes content like legal and government documents, databases of hacked content, medical and financial records, and various forums. Visiting the deep web doesn’t violate any laws. The legality or illegality of any web surfing boils down to what you do while you’re there.
Q: What is a TOR exit node?
A: This network maintains online anonymity through a series of encrypted layers. The TOR browser uses a virtual circuit (VC) of nodes that passes information anonymously from one to the next until the web surfer arrives at his or her ultimate destination. Each node sends just enough data to the next node to make a connection. The final node that your IP request passes through is the exit node. Your original location is not traceable through this node, but any websites you visit with an unsecured http are.
Unfortunately, abuse is possible from any direction. The network keeps a running list of TOR exit node blocks. You can look up them up here.
Q: Is TOR really anonymous?
A: It’s about as anonymous as one can get without additional encryption features. However, it’s not infallible or uncrackable. In fact, some government agencies are going our of their way to locate people who use the network, such as the ND+SA sweeps conducted using their XKeyscore program. It protects IP addresses and locations while one is using the network, but it doesn’t mask traffic as it’s entering or exiting. For complete anonymity, it’s still smart to use additional encryption methods like installing a VPN.
Q: Is TOR dangerous?
A: Using The Onion Network and browser are not dangerous in and of themselves. Danger depends on why you’re there, where you land, and who you interact with when you arrive. Think of the deep web as the shady side of town and be careful who you interact with. Whatever scams and perversions are available on the surface of the internet are exponentially greater once you dip into the depths. See our online safety tips above to learn more.