Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
A Short List of Classical Ciphers

Classical ciphers are ciphers developed prior to the invention of the computer. These are opposed to mechanical or modern ciphers, which require either machines or computers to decipher respectively.
Classical ciphers were used throughout all of history, up until the early days of World War II. They range in complexity from very simple to very complex. Similarly, some have been used by governments and militaries, while others have only ever been used by amateurs for entertainment.
Nowadays, the only reason to use a classical cipher is for entertainment. Even an old, slow computer can break any of these with relative ease. If you need real security, you’ll want to use a modern encryption method. That said, we’ve ordered these algorithms roughly in order of complexity.
Atbash Cipher
The Atbash cipher is probably the simplest in existence. The alphabet is simply reversed and substituted, so A becomes Z, B becomes Y, and so forth. The advantage of the Atbash cipher is its simplicity, albeit that same simplicity is also what makes it ineffective.
Caesar Cipher
The Caesar cipher is a simple substitution cipher, where a letter is shifted either left or right by a certain number of positions in the alphabet. So with a left shift three, D would become A, E would become E, and so on.
ROT13 Cipher
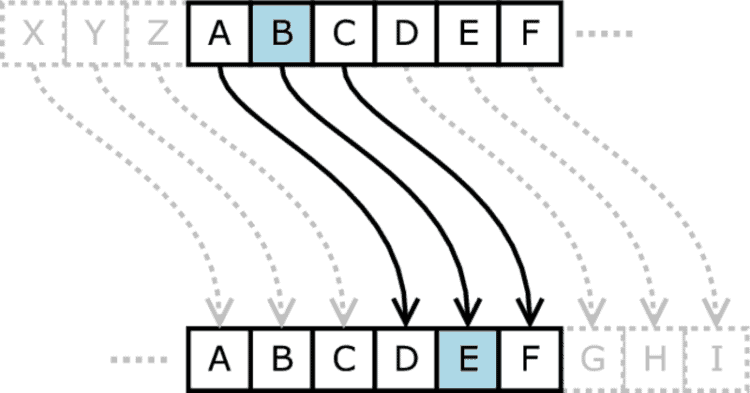
The ROT13 cipher is a variant of the Caesar cipher where each letter is replaced with the letter 13 positions after it in the alphabet.
Because a 13-letter shift in either direction is equivalent, you can easily convert text back and forth.
It’s sometimes used in online forums to obscure joke punchlines or movie spoilers.
Affine Cipher
Affine Cipher is a simple substitution cipher.
Baconian Cipher
The Baconian cipher is a substitution cipher that relies on using two different fonts in the same document. Invented by English Lord High Chancellor Sir Francis Bacon.
Rail-Fence Cipher
Rail Fence cipher is a basic transposition cipher. Instead of the letters themselves being obscured, they’re jumbled up according to an algorithm.
Polybius Square Cipher
A substitution cipher where each letter is recorded as two letters.
Simple Substitution Cipher

A substitution cipher where each letter is mapped to a different letter of the alphabet.
However, the letters are mapped seemingly at random. Decoding requires either a code book or deep analysis.
Codes and Nomenclators Cipher
This is a catch-all term for a variety of ciphers and word substitutions. The system was commonly used during the Middle Ages, in communications between nobles.
Columnar Transposition Cipher
In a columnar transposition cipher, the plain text is written in rows. However, the transposed text is recorded in columns rather than rows.
Vigenère Cipher
Vigenère Cipher is a polyalphabetic substitution cipher. Virtually impossible to decipher without a code book or a computer.
Autokey Cipher

The autokey cipher is similar to a Vigenere cipher, but adds an extra word to the plain text that serves as a key.
This makes it even more secure than a Vigenere cipher.
Beaufort Cipher
Another polyalphabetic substitution cipher, similar to the Vigenere cipher.
Porta Cipher
Similar to an autokey cipher, it’s a polyalphabetic cipher that uses a key word for security.
Running Key Cipher
The running key cipher is a further improvement on the autokey and porta ciphers. Instead of a single keyword, the key is a long string of text. As a result, it offers yet another layer of security.
Homophonic Substitution Cipher
Homophonic substitution ciphers allow you to substitute more than one ciphertext letter for a given plain text letter. This makes it harder to decipher, since mapping isn’t always predictable.
Four Square Cipher
Four Square Cipher is a matrix-based cipher, invented by Felix Delastelle in 1902. Very good at diffusion.
Hill Cipher
Hill Cipher is another classical cipher based on matrix theory.
Playfair Cipher

A Playfair cipher is a substitution cipher, but it uses pairs of letters instead of single letters to represent a single ciphertext character.
Because it uses pairs of characters, frequency analysis code-breaking techniques are ineffective.
ADFGVX Cipher
The ADFGVX Cipher is a fractionating transposition cipher. Each character in the plain text is transposed as a pair of letters, which is then transposed again into the final method. Because this cipher requires two keys, it’s virtually unbreakable without computers.
ADFGX Cipher
The ADFGX Cipher is similar to the ADFGVX Cipher. Both were used by the Germans during World War I.
Bifid Cipher
This is a simple version of a fractionating transposition cipher. Because it takes a lot of time to transpose and is relatively easy to break, it’s only ever been used by amateurs.
Straddle Checkerboard Cipher
A substitution cipher, but different characters can be represented by strings of variable length, making it harder to crack.
Trifid Cipher
An alternate variant of Bifid.
Base64 Cipher
An algorithm for converting text to binary. Formerly used in many computing applications, now only used by hobbyists.
Fractionated Morse Cipher
Text is converted to Morse code, then Morse code blocks of a determined length are converted back to text. Similar in concept to a fractionated transposition cipher, but the “key” in both steps is Morse code.