Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
Network Vulnerabilities List
Cyber crime has been with us for as long as networked systems have been in existence. From hackers looking to see how much trouble they can cause to criminals locking admins out of networks for ransom, the depth and breadth of possible vulnerabilities – and the actions that exploit them – seems almost insurmountable.
Even older exploits with proven fixes are evolving and re-emerging as new threats to overcome. That means network security must be a priority for users, IT professionals, and system administrators alike.
What are the emerging network security threats for 2019 and beyond, and what can we do to prevent them?
What are exploits?
Exploits are actions taken that use systematic flaws and vulnerabilities to gain access to networks and networked devices. They can be launched for purposes of causing mischief, for blackmail, or for financial gain, and the end result will be the same: someone will lose – whether it is their money, their identity, or their reputation.
Exploits usually take the form of malicious code that’s created in order to change the way a system or device operates, giving an unauthorized person backdoor access to databases, programs, or hardware. They aren’t viruses, but a means of delivering a virus. Rather than infecting your computer or mobile device, they install a set of tools that allows hackers to exploit vulnerabilities and do a lot of damage.
It’s like someone breaking the lock on your door so that criminals can come in and steal all of your stuff.
Hackers like to try to exploit high-traffic, popular websites, where they launch an exploit that can redirect the unsuspecting user to a space on the internet where they can scan their system for flaws and vulnerabilities that are ripe for further attack.
They enter systems in one of two ways. Either the code is inserted into the command lines that initiate a request and response between the server and browser or they’re hidden in on-page advertisements. Email attachments and video are also common methods of entry.
In the old days, you had to click on the ad to be redirected to the hacker landing page and scanned, and that’s still common, as Google Double-Click customers learned recently. But, hackers can now redirect traffic without any engagement on the part of the computer user. The most common examples of this are ransomware attacks and cryptojacking.
What’s at risk?
Potentially, any software, network, or device is at risk for exploitation. Some commonly affected targets are Internet Explorer, Flash, MS Office, Adobe Reader, and anything written in JavaScript (JS).
What information are hackers after?
Any kind of information that can be used to harm an individual or organization, that can be used to steal someone’s identity, or allow access to an account. The most common treasures sought by hackers are:
Personal information like names, phone numbers, and addresses
- Biometric data
- Health information
- Account numbers
- Login credentials
- Client lists
- Trade or government secrets
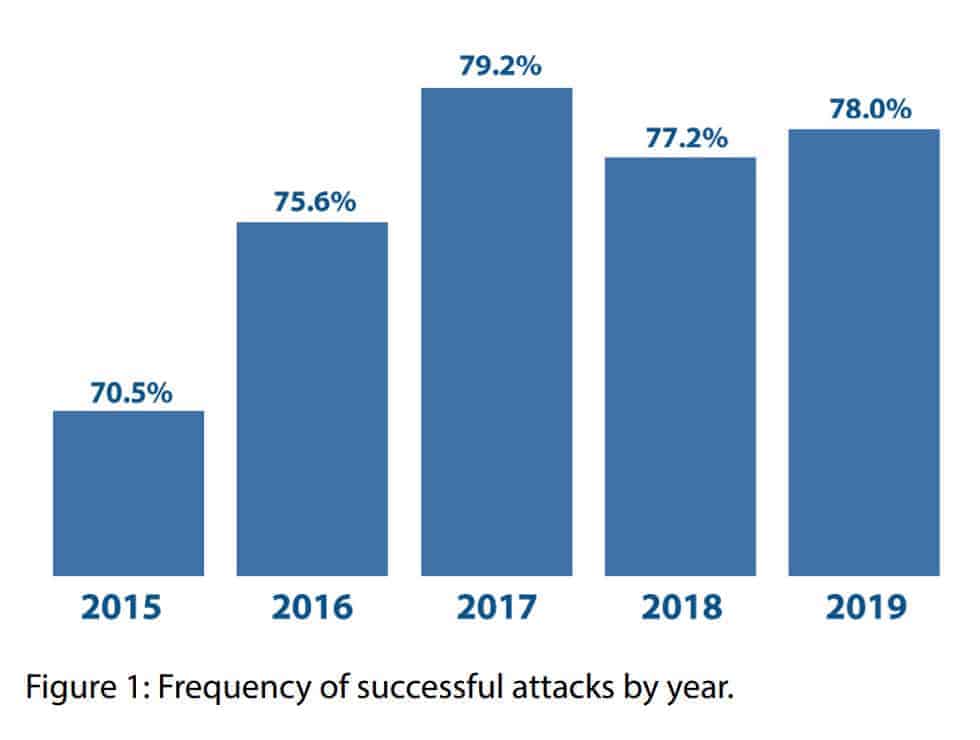
As if headlines about data breaches and ransomware attacks weren’t enough to scare you, here are some sobering statistics that may hit closer to home.
- There is a hack initiated every 39 seconds.
- Most companies don’t even realize they’ve been attacked for almost six months.
- As of April, 2019, there were 24,55 million new samples of malware discovered.
- 93 percent of malware evaluated was polymorphic, meaning it has the ability to transform its code and escape detection.
- 81 percent of all ransomware attacks were against enterprises.
Who’s vulnerable to Cyber Attacks?
Any network, piece of software, or device is potentially vulnerable without the right safeguards in place. It doesn’t matter whether you’re an individual accessing a public network on your smartphone, an employee using your personal device on the job, or even a large corporation utilizing a distributed network on a cloud. If you’re not putting security at a premium, you’re setting yourself and possibly your entire organization up for exploitation.
The good news is that rootkit exploits have leveled off a bit since Angler, the kit responsible for nearly 60 percent of all exploits in 2015, were shut down. This has led many hackers to return to their roots and devise new versions of old hacks.
All this being said, here are the top 10 network vulnerabilities you should be aware of in 2019.
Network Vulnerability 1: Mobile Devices
Exploitability Level: High
Detectability: Average
Potential for Damage: Severe

For the first time since they were introduced to the market, mobile devices have outpaced PCs for usage. Unlike the mobile phones of old, tablets and smartphones have complicated networks that are structured much like traditional desktop computers. Not only do they use complex, multi-threaded operating systems, the popularity and availability of millions of third-party apps means more opportunities for exploitation than any device before them.
As their popularity and use grows, so does the potential threat. People aren’t using them just for personal communications any more. They’re also being used to conduct business in an increasingly mobile workforce.
How does it happen?
Usually, through physical access, either by theft or someone leaving a phone lying unattended, and by social engineering. Another emerging trend is lookalike apps that mimic apps from trusted brands or developers. This was a huge problem with the Google Play store just last year. This trend has a high probability of escalating beyond this year.
How to prevent it
First of all, any mobile device should use 2F authentication to limit access. Companies also need to create strict policies against using personal devices to conduct business, and all work devices should use encryption.
Logging onto unsecured public networks should be avoided, and it’s a good idea to install a quality VPN (French: Meilleur VPN) from a reputable provider. Avoid downloading apps from unknown developers, and make sure the branded app you’re installing is legit.
Network Vulnerability 2: USB Flash Drives
Exploitability Level: High
Detectability: Low
Potential for Damage: Severe

This little peripheral device can carry a load of trouble. For one thing, newer USB drives can contain up to 128GB. That’s a lot of room to camouflage code programs, and malicious commands. Another factor that lends to the vulnerability is the fact that most devices will begin to read and install the data on the drive automatically as soon as it’s inserted.
How does it happen?
It’s really very simple. Hackers install malicious code or a program in the drive, which gets loaded into a laptop or PC. The auto-install feature means that many of these destructive programs and viruses are never detected until it’s too late.
When you consider how many times you’ve plugged a USB stick into your port just to see what’s on it, you’ll realize the potential for wide-spread destruction. In addition to errant USB drives found in parking lots, in drawers, or on desks, many are handed directly to a target by a vendor or work associate.
How to prevent it
The best ways to prevent this type of exploit is to only use a new USB drive to store data, never plug in a stick unless you know the full chain of custody, and disable the auto-run feature on your devices.
Network Vulnerability 3: Misconfigured Firewalls
Exploitability Level: Average
Detectability: Average
Potential for Damage: Severe

This vulnerability was in the news just recently as the culprit in the Capital One breach. In July, it was discovered that an employee of the cloud computing platform that powers the credit card giant used a firewall misconfiguration to access accounts of more than 100 million customers. Misconfiguration of the firewall rule base is the culprit in 95 percent of firewall breaches.
These are not flaws so much as they are mistakes in creating user-defined rules that are set to filter incoming network communications. These rules include an inbound port rule and a list of banned IP addresses. When a firewall is misconfigured, outside actors can access portions of the network that are usually prohibited.
How does it happen?
Typically, it’s due to a mistake in configuration by a network administrator, but this vulnerability can occur when firewalls aren’t monitored, patched, or updated regularly.
How to prevent it
The first line of defense is offense. Make sure that your router’s firmware is updated regularly. Companies should also institute a strict policy regarding firewall management that includes regular monitoring and security patches. Evaluate and update your firewall rule base to reflect current threats and company requirements, and make sure that the policies are implemented.
Network Vulnerability 4: Broken Authentication
Exploitability Level: Average
Detectability: Low
Potential for Damage: High
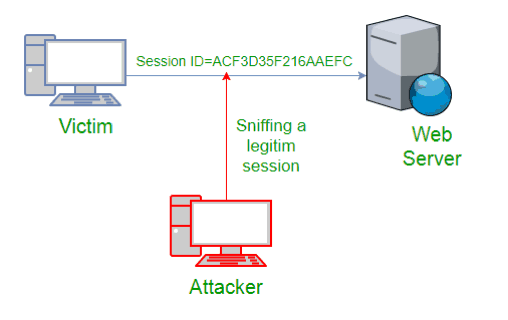
Broken authentication falls under the auspices of proper session management. Such vulnerabilities allow hackers to gain access to a browser session by bypassing or capturing authentication. This allows the attacker to gain access to accounts and databases through a computer user.
How does it happen?
There are several ways that broken authentication occurs. One common method is through URL rewriting. Another is through a so-called “Dictionary Attack”. This is a basic as it sounds. Dictionary attacks occur when a hacker uses a program or manually runs through a list of common or previously used passwords until they strike gold. This is also called a “credential attack”.
Two other common nodes of entry are through unhashed passwords and improper timeout setting.
Is there any way to prevent it?
Developers should test all code during production and perform regular security audits. Admins and users should avoid using default or inadequate passwords, and use multi-factor authentication to limit unauthorized access.
Session IDs should be hidden and not revealed in the URL, they should be recreated after each new login, and session timeouts should be set to expire quickly. All API pathways, credential recovery protocols, and registrations should use the same message for all outcomes in order to harden them against enumeration attacks, and attempts at authentication should be limited to no more than two.
Network Vulnerability 5: SQL Injections
Exploitability Level: Average
Detectability: Low
Potential for Damage: Severe
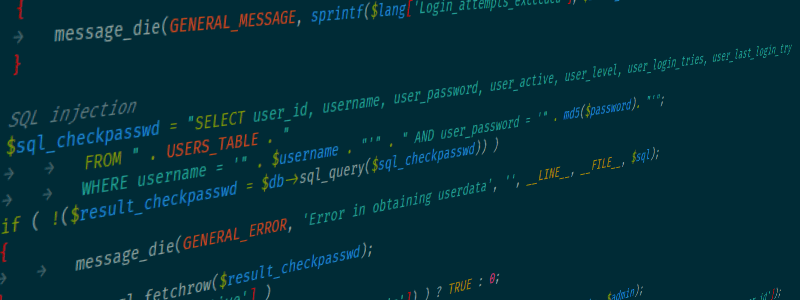
Hackers insert malicious code into browser queries in order to cause mischief like collecting data or damaging networks. Although there are several types of injection attacks, SQL attacks are among the most common. SQL injections cause the code to consume data, according to the Open Web Application Security Project (OWASP).
That attack looks like this:
String query=”SELECT*FROM accounts WHERE custID='”+request.getparameter(“id”)+”‘”;
The “id” parameter value is then modified to initiate the exploit, like this:
https://url.com/app/accountView?id=’ or ‘1’=’1
That code alteration would initiate a command to return all records from the specified database, but the code can be written to cause all kinds of problems.
How does it happen?
Hackers will usually probe networks and coding until they find a weak spot to infiltrate and insert coding. The outcome will be whatever the code details, and the attacks usually go undetected for quite some time.
Is there any way to prevent it?
The best prevention for this type of exploit is to know and deploy security best practices during development. Some of these include:
- Using safe APIs
- Keeping data and queries separate
- Whitelisting server-side input validation
- Using SQL controls like LIMIT to set parameters and prevent mass disclosure.
Network Vulnerability 6: Cryptojacking
Exploitability Level: High
Detectability: Average
Potential for Damage: High

This exploit is surpassing ransomware as the most dangerous digital financial crime, rising by 75 percent last year. Cryptojacking is expected to grow into a lucrative and easy to finesse exploit in relation to how the popularity of cryptocurrency and practices like cryptomining increase.
What does it do? It takes advantage of causal computer users by tricking them into installing software that hides underneath their browsing session, Once it’s there, it discreetly mines cryptocurrency in the background undetected. It’s the kind of low-risk/high-yield crime hackers love.
How does it happen?
Hackers inject JS code into digital marketing ads, malicious links, and websites. Once the target is infected, it can be used to commandeer any device connected to the same network, using their resources to mine cryptocurrency. You might think of it as the cyber equivalent of an accountant skimming spare change from accounts in small enough amounts that it will go undetected for some time.
Is there any way to prevent it?
Some newer versions of web browsers have extensions that are meant to detect and block cryptomining apps. Ad blockers can also be effective. You should avoid suspicious emails and attachments. Tell-tale signs of an exploit include system overheating, sluggish performance, and high resource usage.
Network Vulnerability 7: Data Leaks
Exploitability Level: Easy
Detectability: Average
Potential for Damage: Severe

This is one exploit we hear about all the time. Whether the cause is human error or malicious intent, data breaches are the source of financial ruin and damaged reputations throughout cyberspace.
The data leaked or exposed can be names, phone numbers, access codes, or passwords. Sometimes, the motive is just exposure in order to prove that it can be done or by a disgruntled employee. Other times, the information is sold on the black market or used to access bank accounts for financial gain and health records for blackmail or espionage.
How does it happen?
Hackers probe databases and networks looking for flaws and vulnerabilities. Once they uncover a weakness, they’ll access data through direct brute force attacks or by backdoor access. A very simple way of accessing information is to monitor traffic and steal session cookies. They will then spoof the cookies and hijack the session to change information like passwords or rerouting bank funds. There are many other variations.
Even when data is properly encrypted, that protection can be broken by weaknesses in common areas like key generation, protocol deployment, and database management.
How to prevent it
Data protection should be the number one concern of anyone who uses a computer. The easiest and most common way to do this is by encrypting all data, controlling access, and segmenting databases into a hybrid cloud storage model that places the most sensitive data on a private, on-site storage. You should also classify data according to sensitivity, and institute a least privilege access model.
Network Vulnerability 8: XML External Entities (XXE)
Exploitability Level: Average
Detectability: High
Potential for Damage: Severe

This exploit takes advantage of a security flaw to interfere with XML processing. Such attacks are becoming more common in large, popular web applications like social media platforms.
How does it happen?
Usually, it’s performed in two parts that must co-exist. First is a weak or misconfigured XML parser in the application code. Second, there needs to be a reference inserted to an external source that’s misread by the flawed XML parser. This will allow Denial of Service (DoS) attacks, data breaches, or forgeries in the server-side request.
How to prevent it
The most direct way is to disable external entities altogether. That has the added bonus of eliminating the possibility of DoS attacks. If external entities aren’t disabled, then developers should learn to detect the signs of a weak or inadequate XML parser.
You can also use some form of verification to ensure that xml/xls files are validating the XML.
Network Vulnerability 9: Cross-Site Scripting (XSS)
Exploitability Level: Average
Detectability: Low
Potential for Damage: Severe

An XSS exploit was responsible for the Google Double-Click exploit when hackers used it to redirect users from eCommerce websites to their own landing pages. Because they occur in the end-user side, they can go undetected for a long time.
How does it happen?
Through mechanisms like comments, submission forms, and similar vehicles, hackers are able to inject malicious code into an app or web page. The code then modifies queries, causing the server to respond and do the criminal’s bidding instead of the website owner’s. In the Double-Click fiasco, legitimate Google partners were losing PPC revenue through third-party advertisers that experienced XSS exploits.
The users never realized they were being redirected to someone else’s landing page or ad, and most of the legitimate owners didn’t either until they noticed their revenue didn’t match their traffic.
How to prevent it
The issue with the Google attack was the frameworks used by the third-party advertisers. Safer frameworks like those used in Ruby 3.0 or React JS will allow the XSS to escape.
You can also use coding that’s sensitive to context on the client side whenever possible, or via the API otherwise. Admins can create and implement a Content Security Policy (CSP) that’s geared toward avoiding XSS exploits.
Network Vulnerability 10: Internet of Things (IoT) Networks
Exploitability Level: High
Detectability: Low
Potential for Damage: Severe

The internet of things is one of the fastest-growing networking systems for home and business automation. It’s very convenient, but it can also be deceptively vulnerable.
Most people know to protect their mobile devices and business networks. But, how many worry about their thermostat or home theater setup? The things you’re least concerned about protecting could provide a gateway into your bank accounts or home security system.
How does it happen?
Access is gained through unsecured WiFi connections, weak access protocols, outdated firmware, and a whole lot of other basic security practices that people don’t think to implement on their home appliances.
Trouble is, those benign household aids are usually connected on the same network that holds access to your bank account, credit card information, and all kinds of other cyber loot.
Is there any way to prevent it?
First of all, mind your financial adviser and diversify. Not your accounts, but your networks. That means to configure routers for separate networks whenever possible so that all of your IoT eggs are not in the same basket. If one component gets hacked, it won’t lead the intruder straight to your bank.
End-to-end encryption installed on your router and each device connected to your networks is also standard practice. Get rid of all default passwords and replace them with ones that are strong and difficult to guess. Lastly, make sure that all firmware is updated and patched as soon as new fixes are released.
Keeping Your Networks Safe
Although we’ve tried to offer some relevant advice regarding each vulnerability, there are some general rules about prevention that will keep your data and networks safer.
- Make sure to keep all software, anti-virus, and firmware updated.
- Uninstall old, unsupported, and unused plugins and themes rather than simply disabling them.
- Invest in the most current and comprehensive cyber-security protection available.
- Conduct a complete security audit at least twice a year.
Frequently Asked Questions About Cyber Security Threats
Sometimes, you just need a few quick answers to basic questions. We offer four of the most common questions about cyber threats and the answers you need.
Q: What is the difference between vulnerability and exploit?
A: Vulnerabilities are weak points in software or networks. Exploits are malicious actions that take advantage of these vulnerabilities. Although vulnerabilities are usually found in older programs, networks that haven’t been updated, or very complex systems, they’re still common and can be present almost anywhere that security is lax.
For example, if authentication is broken, a hacker can take advantage of that flaw to gain access or even take control of the system.
Q: What is a rootkit vulnerability?
A: Rootkits are programs created by hackers that are designed to target and infect a device. Once the program is released into the system via a link containing the code, it installs tools that will allow the attacker to access the system or device remotely. This means that the attack can be initiated from any location. Although this exploit was once targeted to PCs, it’s become more common with mobile devices as they increase in usage.
Q: What does DDoS attack mean?
A: Distributed denial-of-service (DDoS) attacks are exploits that strain network resources to the point of causing the system to crash. This is most commonly achieved by flooding a network with so much traffic it overcomes the available bandwidth or memory. This type of attack can be used by a single hacker using a program that sends thousands of requests to a single server or by multiple agents sending requests repeatedly.
Q: What is the purpose of a vulnerability assessment?
A: This is a procedure that probes and tests a system in order to identify flaws that could allow malicious actors to penetrate the network or device. Cyber security professionals perform such assessment in order to obtain a deeper understanding of potential vulnerabilities and devise a means of preventing security breaches and data leaks.
Final Thoughts
The fact that you haven’t been the victim of an exploit yet doesn’t mean it’s okay to let your guard down. Apathy leads to inaction, which can lead to you becoming another cyber crime statistic.
A network vulnerability that goes unchecked is a cyber crime waiting to happen. As IT security professionals, it’s up to us to remain one step ahead of the black hats. Knowing the threats that are out there and where they’re emerging from is the first step in prevention.
Educating computer users, network administrators, and developers raises awareness of potential problems. The final stage in preventing network vulnerabilities is developing solutions that are effective, using advanced techniques like AI and strong encryption.
Related: Cybersecurity AI vs. Malware AI
Cyber crime is never going to go away. But, diligence and awareness will go a long way toward reducing the risks and potential outcomes of such exploits.




