Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
Guide to Hash Functions and How They Work
Digital data breaches have become so commonplace that they do not raise too many alarms unless you were one of the millions of LinkedIn users who were exposed or if your old MySpace account got hacked. All of these breaches run together in a cryptic blur for most people who don’t realize what these companies did wrong to offer up your information to cyber thieves. One of the many reasons this may have happened is because your information was not properly hashed.
Hash can be used interchangeably as a noun or verb in cryptography. Hashing is the action of changing passwords into unrecognizable strings of code that are designed by impossible to convert back. These are also called hashes. Some hashes can be cracked more simply than others, but it’s still a difficult task that most novice hackers won’t be able to do.
Why is Hash So Important
Most hackers want to use data to access user information, and to do so, they most often need your password. What these criminals find and defraud from your profile is not stored in a form that is readable by the naked eye, unless the company does not protect their sensitive data.
Your password is converted into hashes typically the very moment you create one, and it looks like a random set of strings. It’s your password mathematically transformed into something unhackable. In most cases, it takes years to decipher a hash, and by then, you could have already changed the password or deleted your account.
What are Hash Functions
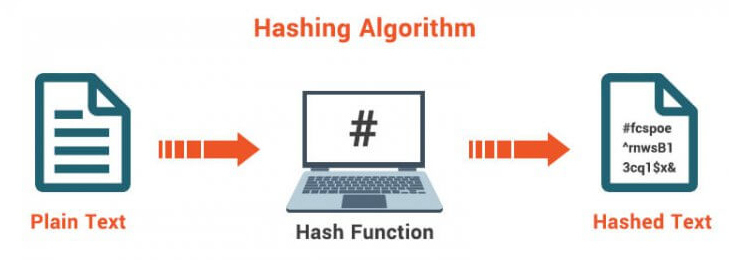
Hash Functions – These are functions or techniques used to encode passwords and other plain text into unreadable text for storing and transmitting. There are many types of Hash functions based on the way the plain text is encoded.
What Hash Functions Are – These are functions or techniques used to encode passwords and other plain text into unreadable text for storing and transmitting. There are many types of Hash functions based on the way the plain text is encoded.
How are Hashes Designed
A hash is designed to be a one-way function, which is a mathematical operation that is simple to perform at first, but it cannot be reversed. Once you hash the raw data, it becomes complete gobbledegook, which is how your account remains protected from hackers.
Hashes are not designed to be decrypted in any way. Once you enter your password, the system performs the hash and checks the results against the hash that was created of your password when you first set it. It verifies the password without having to store it in the system, which is another reason that hackers hate websites with hashing.
Differences Between Strong and Weak Hash Methods
In theory, no one should ever be able to crack a hashed string, not even the company storing the hash. No one will ever be able to convert a stored hashed password back into the original password. However, hashing schemes have been around for many years, and some have become weaker than others.
For instance, the case of 177 million LinkedIn accounts going up for sale on the dark web shows that hashed passwords can be cracked. LinkedIn had only used a simple hashing function at the time called SHAI, and it had no other protections in place to prevent data from being stolen. This allowed the hackers to access passwords and also try those passwords on other websites. This may have been the reason why Mark Zuckerberg’s accounts for Twitter and Pinterest were hacked at the same time.
Another case of hashing gone wrong is the story of Patreon’s data breach. This time, the website had very strong hashing functions in place called bcrypt. This function provides some more time between the breach and changing the passwords before the hacker can get to all of the cached data.
So what’s the difference between SHAI and bcrypt? With SHAI, hackers are not able to reverse the hashed password created with that specific function. However, they can guess passwords and run through the same function to discover the password and how it’s hashed.
When they get a matching hatch, they can use a hash-cracking program to filter through much larger databases and guess millions of passwords or more. They can then use that data to compare with results from a group of hashed passwords to find more matches, thus leading to a dominos effect if you use the same password for every site. Good job, Mark Zuckerberg!
What are the Characteristics of a Useful Hash Function
Since there are several different hashing functions out there, it’s best to look for ones with these four characteristics.
Efficient and Fast
No one wants to wait to log in as their password is hashed. This means that the hashing function must be efficient and quick. Since hashing function can be laborious, it’s imperative to find the fastest one. If a typical computer needs several minutes to process a hashing function and create an output, then it would not be practical for the business. Most computers today can process a hash in a fifth of a second.
Always Gives the Same Result
Hash functions also have to be deterministic. For any input provided, the hashing function must always provide the same result. If you plug in the same input 5 million times, one after the other, the hash function should produce the same exact output 5 million times as well.
If a hashing function were to create different results every time that the same input was plugged in, then the hash would be too random and useless. It would be impossible to verify the provided input as well, which is the whole point of hashed passwords.
Pre-Image Resistant
The result of any hash function should not reveal any information about the provided input. This is known as pre-image resistance. While cryptographic hash functions may receive any kind of information, whether it’s letters, words, punctuation marks, or numbers, the hash function must always put out the same fixed-length result. This is true even if you input an entire book of characters.
This is to conceal any hints as to what the input is. It must be impossible for hackers to guess what was originally provided. Therefore, it is impossible to determine whether the string is long or short.
Collision Resistant
The last characteristic defines how unlikely it will to find two different inputs that create the same result. This means that there are any number of inputs that can be made, but the outputs are still fixed length. There are also a lot of outputs that a hash function must produce, but the number is finite in contrast to inputs, which can be infinite.
Simply put, the goal is to make finding two inputs that create the same output absolutely impossible, and that the probability of it can be dismissed before any risk is even assessed.
Why are Hashes Irreversible
Why Hashes are Irreversible – Hash functions are usually one-way due to much of the plain text being discarded during the encryption process. Matching is done by putting the user text through the hash function and comparing it to the encrypted text.
What is a Hash Collision Attacks
Hash Collision Attack – A hash collision refers to two input texts having the same output after encryption. This is called a collision and attempting to find such strings are called hash collision attacks. This is highly unlikely given the complexity of current hash keys.
Understanding Password Salting
Password Salting – Salting refers to appending an additional string to a password before encrypting it. This makes it difficult for attackers to identify passwords based on a precomputed table of passwords called a rainbow table.
What is Hash Peppering
Cryptographers like to season their hash with another spice called “peppering.” This is similar to the salt technique, except that the new value is placed at the end of the password. There are two versions of peppering. The first is a known hidden value that is added to each value, but it’s only valuable if not known by the hacker.
The second is the value that is randomly generated by the system, but it isn’t stored. This means that every time a user tries to log in, it has to try multiple combinations of the hashing algorithm and the pepper algorithm to find the right values that match the hash. This means it can take a long time to log in, which is why it isn’t used.
How Password Storage Works with Hash Functions
How Password Storage Works with Hash Functions – This refers to storing user passwords in an encrypted manner to ensure that external parties are unable to manipulate the user’s login in case the database is compromised.
How Do Rainbow Table Attacks Work
Rainbow Tables – This is a table of passwords and their output when encoded using many known hash functions. Such tables are used to identify passwords without having to spend time on computing hash functions.
What Tools are Needed for Hash Functions
Tools Needed for Hash Functions – Different types of hashing functions are available as online tools where plain text can be encrypted by simply copying them into a given text field. MD5 and SHA-256 are some of the more popular hashing functions.
Understanding Classes for Cryptographic Hash Functions
There are several different classes of hash functions available. However, there are few more common ways used today, including:
- BLAKE2
- Secure Hashing Algorithm or SHA-2 and SHA-3
- RACE Integrity Primitives Evaluation MEssage DIGEST or RIPEMD
- Message Digest Algorithm 5 (MD5)
Each of these classes involve hash functions with several different algorithms combined. With SHA-2, a family of hash functions was developed to make it more difficult to crack. This includes SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256.
While each varies from the other in the way that they transform a given input, they also have varying fixed lengths that they produce after digesting the input. For example, SHA-256 is used the most in blockchain technology, and it is based upon the original Bitcoin code.
How are Hashes Processed
In a word, instantly. For a detailed explanation, the process is a bit more complex though it is completely automated and happens in seconds. This process is also called the Avalanche Effect or Butterfly Effect.
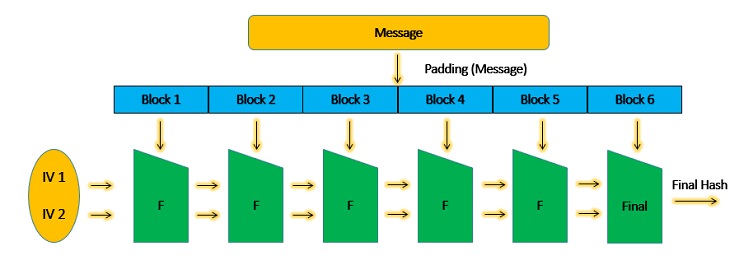
Basically, the size of the data block differs from one hashing algorithm to the next. For a specific algorithm like SHA-1, the message or password is accepted in blocks that contain 512-bits only. This means that if the password is only of 512-bit length, the hash function would only run one time. If the message is 1024-bit, then it is divided into separate blocks of 512-bit each. The hash function also runs twice.
In most cases, a technique called Padding is also used, which means that the entire message or password is divided into equally sized data blocks. The hash function is then repeated as many times as the total number of blocks. These blocks are processed one after the other. In this process, the output of the first data block is fed as an input along with the next data block.
The output of the second is then fed to the third block, and so on and so forth. This makes the final output the same number as the total value of all the blocks together. If you change on bite anywhere in the password or message, the entire hash value would also change, hence the name Avalanche Effect.
Wrapping Up
If your password is properly hashed and salted, then the only way to get through would be a brute force attack. With longer passwords that have more encryption, the brute force attack takes longer, meaning that it’s more time-consuming and costly to the hacker.
This means that your users should always create longer passwords and configure with secret characters, such as a symbol or capitalized letter. This is also why randomly generated password strings are more secure than a dictionary word, since brute force attacks utilize dictionaries to find words to test.
When signing up with any online business, you should always check to see how they handle their passwords. Are they encrypted? Are they hashed? How will your information be protected? Most companies with hashing list this in their privacy policies.