Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
Password Salting
Password salting is the process of securing password hashes from something called a Rainbow Table attack. Such was the case with the notorious 2012 Linkedin password breach.
The problem with non-salted passwords is that they do not have a property that is unique to themselves – that is, if someone had a precomputed rainbow table of common password hashes, they could easily compare them to a database and see who had used which common password. A rainbow table is a pre-generated list of hash inputs to outputs, to quickly be able to look up an input (in this case, a password), from its hash. However, a rainbow table attack is only possible because the output of a hash function is always the same with the same input.
So how do we make each hashed password in a database unique? We add something called a salt to the input to the hash function. A salt is basically some random data that is unique to each user, that is saved with their password and used in the hashing process of both storing and verifying the password. The most popular commercial password managers all salt users passwords by default. Why is this effective?
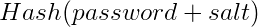
Every user now has something that is unique to them, that is added on to their password before it is hashed and stored in the database. Now, if someone were to try to compare the database password hashes with a list of common password hashes – none of the hashes would match, even if users had used common passwords in the attackers list. The salt completely changes the output of the hash function, meaning that an attacker would have to brute force the password of each user individually, effectively eliminating the benefit of a rainbow table.