Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
VPN Protocols – Different Types Compared
As more Canadians understand the need to protect their online privacy and security with a VPN, they are becoming more sophisticated in regard to the characteristics they are looking for in a reputable VPN.
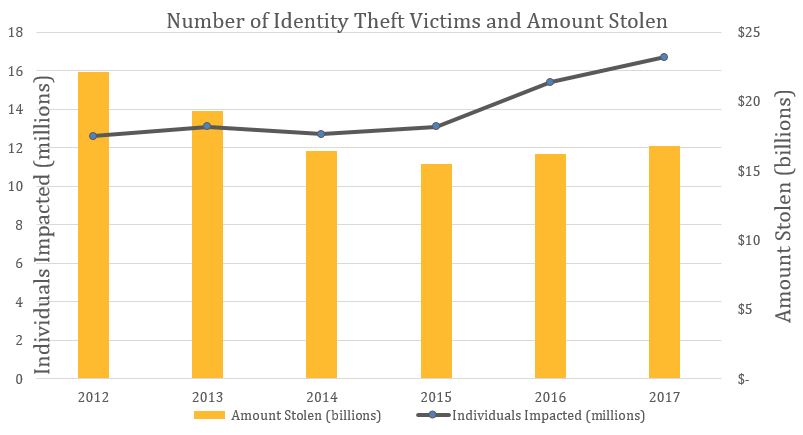
The risk of data hacks and identity theft, which is on the rise, demonstrates the need for a VPN.
One of the most critical features that it makes sense to consider is the protocols that the VPN provider makes available to users.
What are VPN protocols? Most people who are new to the idea think that this is an incredibly technical term that can have little impact on their browsing experience. The reality is that the protocol used by your VPN can make a significant difference as far as how truly safe and secure you are when you’re online.
Let’s take a closer look at what VPN protocols are and how they affect your online experience. Then, we’ll explore the most common protocols that are available today so that you can make a wise decision.
What are VPN Protocols?

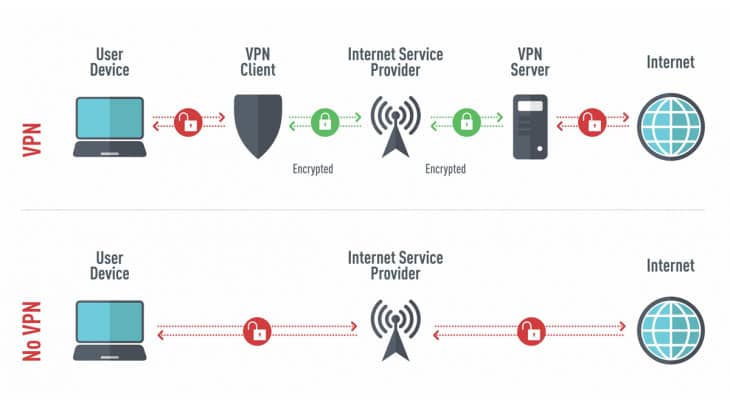
A VPN essentially establishes a tunnel between your computer and the Internet. Within this tunnel, you get to stop DNS leaks. Your true IP address is fully protected; the VPN tunnel masks it with the server’s IP address, essentially making you invisible. It makes it appear as if you are browsing from a location other than your actual location.
Several methods for establishing a VPN tunnel are available. Some of these have been around for many years and are not considered particularly secure any longer. Others are quite new and offer the absolute best available security.
When you sign up with a VPN, you may be presented with numerous VPN protocols from which to choose. How do you know if one of them is an older protocol with less robust security features? More importantly, how do you identify the one that will provide you with the absolute best protection regardless of what you do online?
Most VPN providers offer a choice between PPTP, SSTP, L2TP/IPSec, WireGuard, SoftEther, IKEv2/IPSEC and OpenVPN protocols. After reading a description of each, you’ll be able to make an informed choice regarding which protocol is right for your purposes.
PPTP Protocol
Developed by Microsoft, Point-to-Point Tunneling Protocol, or PPTP, is one of the earliest VPN protocols, yet it is still in use, though has become increasingly rare. Nonetheless, certain VPNs that are determined to offer their users the greatest number of options are still making it available.
Even though PPTP may be available, it is not recommended for regular use by security experts today, as it is rife with security vulnerabilities that might well leave you exposed just when you most need the protection of your VPN most.
In its favor, PPTP is compatible and natively available in all versions of Windows. Most other operating systems can run it as well. Data transfer rates are fairly fast with PPTP. However, if the connection gets dropped, it may be difficult to reconnect.
If keeping your online activities strictly private and anonymous is important, and let’s face it, that’s why you’re using a VPN in the first place, then you should not opt to use PPTP. On the other hand, if your goal is to be able to stream American Netflix as a Canadian, then PPTP just might be sufficient for your purposes, thanks to relatively good speeds.
Nonetheless, do not make it your default protocol. Doing so may leave you vulnerable to hacking, malware, and spying by third parties.
SSTP Protocol
Secure Socket Tunneling Protocol is another product of Microsoft. Unlike many other VPN protocols, it is only compatible with devices that run Windows. This means that it is not among the most widely used protocols. Nonetheless, it is not plagued with known security issues the way that PPTP is.
SSTP relies upon the Secure Socket Layer, or SSL, protocol for moving online traffic. People who are dealing with serious network restrictions, such as those that are imposed in totalitarian states like China, may find that this is a significant advantage.
Users faced with a controlling government regime or who find that other VPN protocols are routinely blocked on their system may find that SSTP is a perfectly acceptable solution. It’s stable, fairly fast and relatively secure. It also allows VPN users to unblock websites and other similarly restricted content. Unfortunately, there are only a few VPN providers that actually support SSTP.
If you have access to a superior protocol like OpenVPN, however, it would be wise to choose that one instead as opposed to SSTP.
WireGuard Protocol
WireGuard is a relatively new protocol with which developers are still experimenting. Because it is in the early stages of development, WireGuard has not yet been audited by a third party. Additionally, privacy advocates have concerns regarding whether or not the use of WireGuard will require logs. These concerns may be moot for the time being as so few VPN providers actually make WireGuard an option.
In fact, many of the VPNs that are making WireGuard available are doing so on a testing basis, meaning that users are essentially helping with the development process. This means that there may be security issues, so it is not wise to use WireGuard when you’re doing something really sensitive.
WireGuard is being developed with the hope that it will offer superior speed, performance, and security when compared with the other available VPN protocols. It is advertised as being a better option in terms of battery consumption, and mobile device users may love that WireGuard promises the ability to move from one network interface to another without losing the connection.
WireGuard cannot be wholeheartedly recommended at this time because it is still under development. Nonetheless, if it is able to someday deliver on its promises with regard to speed, performance and security, it will certainly be a worthy successor to OpenVPN.
SoftEther Protocol
SoftEther is one of the few, newer VPN protocols that are starting to give OpenVPN protocol a run for its money. It was a project developed by students of the University of Tsukuba, but it has become a widely used VPN protocol in recent years.
SoftEther is open source technology, much like OpenVPN. This means that it has been tested, audited, and developed by experts the world over. Advocates appreciate that SoftEther works on a multitude of operating systems, even some that are not served by many other protocols.
These operating systems include the usual like Mac, Windows, and Android but also include Linux, Solaris, and FreeBSD.
SoftEther is even compatible with other VPN protocols like OpenVPN, L2TP/IPSec, and others. Users frequently set up SoftEther on their operating system and concurrently use another VPN protocol, which means that they are protected no matter what happens. Because it is so incredibly flexible, SoftEther is quickly becoming popular.
This VPN protocol is capable of bypassing most firewalls, and it is certainly fast. However, you don’t have to worry that you’re sacrificing security for speed. SoftEther uses AES 256-bit encryption, which also is used by major government and military agencies.
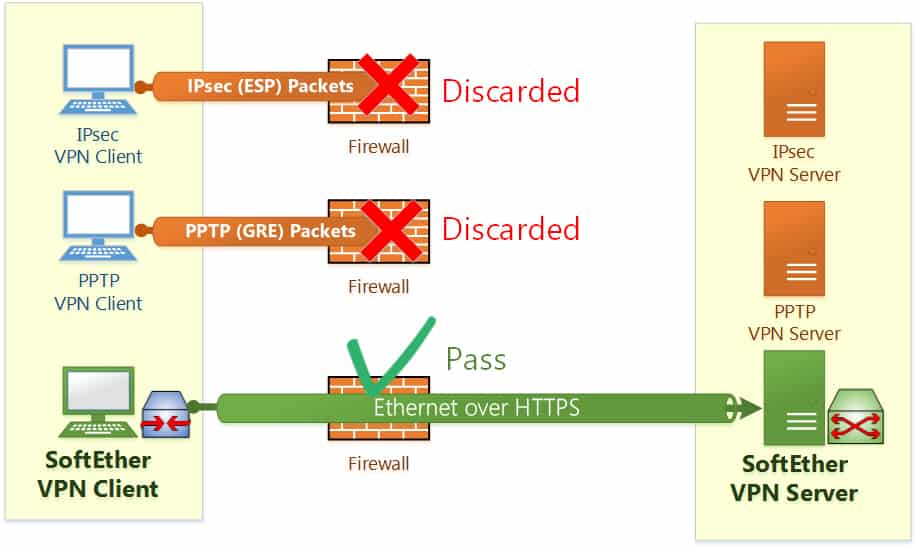
Still, SoftEther is not without flaws. It is fairly new technology so it has not been as extensively tested as the OpenVPN protocol. Moreover, it is not available on many VPNs. This remains an alternative to look out for in the future.
IKEv2/IPSec Protocol
Internet Key Exchange version 2, or IKEv2, is a joint project of Microsoft and Cisco. IKEv2 is basically a tunneling protocol. To make it especially secure, it is paired with Internet Protocol Security or IPSec. This technology encrypts and authenticates data packets that are being sent via an IP network.
The Internet Engineering Task Force developed IPSec to have native compatibility with a wide variety of operating systems. Accordingly, it is not necessary to have a third-party app to run IPSec as it is with OpenVPN and other protocols.
IKE technology has been around since 1998. The current, second version was introduced in 2005. Comparing IKEv2 with other VPN protocols reveals that it can offer benefits to users as far as its ability to establish a connection, its speed, its stability, and its security. Native support for IKEv2 is found on devices running Mac OS 10.11 or more recent, Windows 7 or more recent, iOS, Android and Blackberry.
Some privacy advocates that worry about dangerous cyber security risks are concerned about IKE technology because it is closed source software. This means that it was developed by Microsoft and Cisco without input from independent developers.
Security experts are concerned that this means that IKEv2 may have vulnerabilities that the developers have not discovered. However, the technology has been around long enough that third parties have created open-source versions. Some of these independent versions may offer even more robust security than the original.
IKEv2/IPSec is a recommended VPN protocol, but OpenVPN generally is considered superior.
L2TP/IPSec Protocol
Like IKEv2, Layer 2 Tunneling Protocol, or L2TP, typically is partnered with IPSec to provide an extra level of encryption and security. Also like IKEv2, L2TP/IPSec is natively compatible with many of the most common operating systems.
Devices that are running Windows 2000/XP or newer, Mac OS 10.3 or newer or Android should have a quick and easy set up with L2TP/IPSec. Gaining access to this protocol is as simple as importing the necessary files from your VPN.
L2TP also was developed by Microsoft and Cisco. This means that it’s a closed source software and may have vulnerabilities that have not been identified. L2TP isn’t as popular as IKEv2, which means that it hasn’t been as closely vetted by independent developers. Weaknesses may leave you open to inadvertently disclosing your IP address.
If you’re really concerned about maintaining privacy, then you’ll appreciate that L2TP encapsulates data two times. However, this double encapsulation has a tendency to slow down processing a bit.
By contrast, L2TP/IPSec performs encryption and decryption in the kernel, which may provide improved speed. Will using L2TP/IPSec slow down the performance on your system? The answer can vary. You may need to try it to see how well it works for you.
Overall, the IKEv2/IPSec and OpenVPN protocols are more highly recommended than L2TP/IPSec. If you cannot get access to these other protocols, L2TP/IPSec still is a better choice than some older, less robust protocols.
With many of the most highly-recommended VPNs, you’ll have your choice of protocols. This could be a distinct advantage as it is possible that one protocol will perform better for certain applications than it does for others.
OpenVPN Protocol
Originally developed by OpenVPN Technologies, this protocol is open source. This means that developers all over the world have contributed to perfecting it, looking for weaknesses and vulnerabilities so that they can be eliminated. The result is an incredibly safe and versatile environment for exploring the online world.
OpenVPN is generally regarded as the safest protocol available today, and it is widely used. It’s been audited several times by third-party security firms, so you can trust it to keep your data safe. In fact, OpenVPN is considered the industry standard, especially when it is used in conjunction with SSL/TLS key exchange.
Most reputable VPN providers make OpenVPN protocols available to clients. It is likely to be the default choice. If it’s not, then users are recommended to update their settings. OpenVPN is compatible with all platforms including Mac, Windows, Linux, Android, and iOS. It also works in conjunction with various routers.
Final Thoughts
OpenVPN is particularly safe and secure when used with User Datagram Protocol, or UDP, instead of Transmission Control Protocol, or TCP. Using TCP may mean slightly slower transmission rates.
Nonetheless, OpenVPN remains stable and reliable. Using TLS protocols and the OpenSSL library for encryption means that OpenVPN is exceptionally adept at keeping data secure.
If you want complete protection, consider using a top-notch private search engine when browsing the web. This will anonymize all queries, eliminates the need for cache, and protects you from intrusive ads while providing advanced website threat detection.