Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
What is AES Encryption? A Beginner Friendly Guide
Keeping data secure is a primary concern for anyone who uses the Internet. From the NSA and the FBI to soccer moms and do-it-yourself investors, all of these users are able to function with more peace of mind thanks to data encryption.
AES encryption is the most widely used standard around the world. Unless you are really into this techno-geek stuff, you probably aren’t sure what that is even if you’re using it right now.
How and why is AES encryption so pervasive?
Where did it come from, and why is it such an essential part of a safer online experience?
This article will answer these questions so that your online wanderings will be more secure and private.
What Exactly Is AES?
AES is an acronym for Advanced Encryption Standards. People who are really into this technical stuff also may refer to it as Rijndael. It’s used around the world to encrypt and decrypt highly sensitive data. Governments and the military use it because it’s the best encryption protocol available today.
AES relies on a block cipher algorithm (more on this later) to safely encrypt sensitive data.

To understand AES, it’s necessary to go back to the beginning, to a time the world relied on DES.
The Transition from DES to AES
Almost as long as there have been computers, organizations have sought better ways to protect and privatize their data so that no one can spy on their operations or use their data for their own nefarious purposes.
Back in the early 1970s, computing giant International Business Machines, otherwise known as IBM, introduced Data Encryption Standards, or DES. They based their innovation on an algorithm developed by Horst Feistel.
IBM sent its DES algorithm to the National Bureau of Standards. This organization worked with the NSA to refine the algorithm. By 1977, they had published it as the Federal Information Processing Standard.
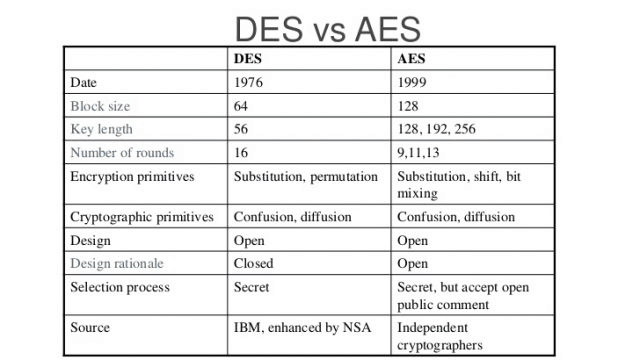
DES performed well for two decades. However, new developments in technology were outstripping its capabilities. The Electronic Frontier Foundation worked with other like-minded groups to break a DES key in January 1999. They were able to do so in just 22 hours and 15 minutes.
Clearly, it was time for encryption standards to take a leap forward. The National Institute of Standards and Technology took the reins. Over a five-year period, they evaluated more than a dozen algorithms that had been submitted as possible replacements for DES.
The National Institute of Standards and Technology didn’t do their work in a vacuum. They invited all sorts of privacy and cryptography experts and organizations to assist with the process of evaluating the algorithms.
Factors such as the strength of the encryption, versatility, and speed all were evaluated. While many were effective, the experts agreed that the submission from a pair of Belgian cryptographers was superior to the others. This was the Rijndael cipher. Upon its acceptance, it was renamed Advanced Encryption Standard, and it began to be used by organizations like the NSA for guarding top-secret information.
How Is AES Used?
AES is free for anyone to use in any way that they like. It is secure enough for federal governments and military organizations around the world, which means that it’s safe enough for you to use as well. In fact, you probably use it regularly, though you may not be aware of it.
Let’s look at some of the most common uses for AES today.
Tools for Archiving and Compression
If you have ever downloaded or received a compressed file, this compression likely was achieved via AES encryption. Compression is used to minimize the size of large files so that your hard drive is less affected when receiving them.
RAR, WinZip, and 7 Zip all are common programs for the compression and decompression of files, and each of them uses AES encryption. Using these tools allows you to bypass completely erasing your hard drive while formatting it, bypass the whole process by keeping zipped files instead of whole ones.
Partition and Disk Encryption
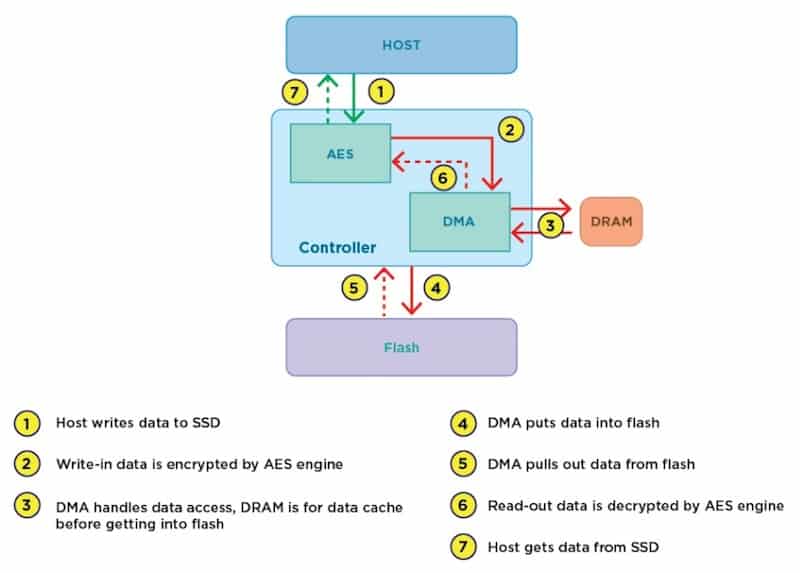
Some people use disk and partition encryption to further protect the files on their computers. Examples of these programs include CipherShed, FileVault and BitLocker. All of these use AES encryption.
Virtual Private Networks
Virtual Private Networks commonly referred to as VPNs, really go the extra mile when it comes to protecting your data. One of the ways that they do this is with the AES algorithm.
If you are unfamiliar with VPNs, then it’s worthwhile to get acquainted with the basics. Think of a VPN as creating a tunnel between your computer and where you want to go on the Internet. The VPN connects you to an encrypted network. This encrypted network is housed on a server that the VPN provider owns.
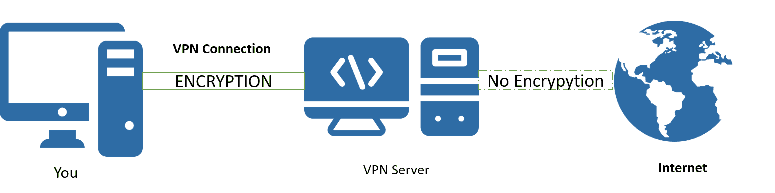
Typically, the VPNs with the best reviews offer customers their choice of thousands of servers located around the world. This makes it possible for the user to make it look like they are browsing from Finland when they’re really in Vancouver, B.C. It may get you around regional content restrictions as well.
Of course, the most important reason to use a good VPN is that it protects your privacy and anonymity online. No one can track where you go, so they won’t know which websites you visit or what you do while you’re there. Your IP address is masked, and all data transfers are encrypted.
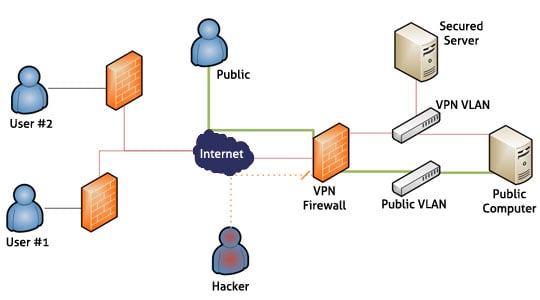
Our recommended VPN services use AES encryption to protect their users. When looking for a VPN, be sure to choose one that uses this encryption algorithm. Other VPN providers rely on PPTP or other outdated encryption methods that won’t truly protect your data.
Look for AES 256-bit encryption to ensure a fully private browsing session. A few examples of VPN services that use AES 256-bit encryption areSurfshark and NordVPN.
A Multitude of Common Applications
AES crops up in all sorts of software and websites that you may use on a regular basis. Online gamers benefit from it, and so do people who use some of the best password managers.
Various social media platforms like Facebook and WhatsApp use AES to encrypt messages too. Clearly, you use AES all the time, so it’s helpful to understand how it works under the hood.
The AES Algorithm
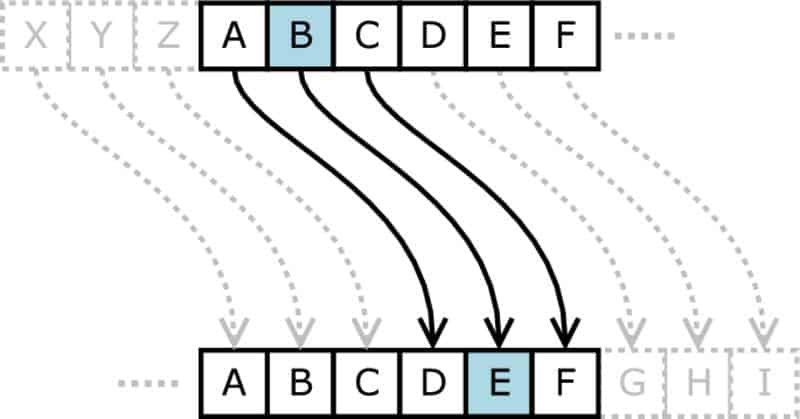
AES is a block cipher in which all data is encrypted in “blocks.” Each block is made up of a predetermined number of “bits.” Each block is 128 bits long, so each time 128 bits of plaintext is submitted to the program, 128 bits of ciphertext is generated.
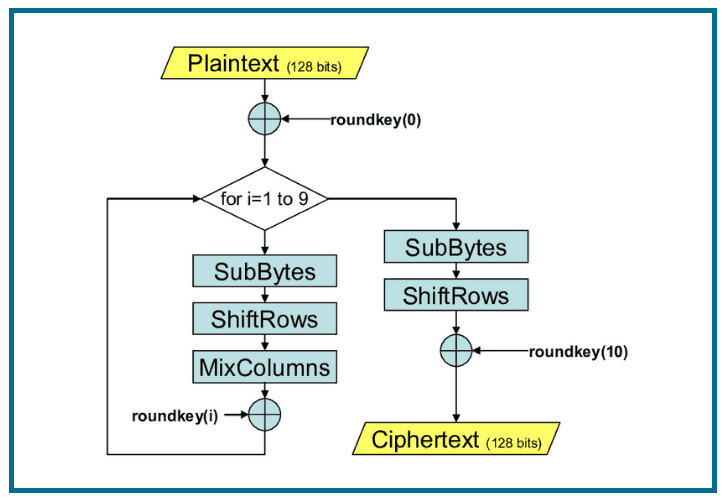
Keys are used for encrypting and decrypting data. Because AES is a symmetric cipher, the same key may be used to both encrypt and decrypt information. The cryptography community recognizes that AES operates on a “4 X 4 column major order matrix of bytes.” This is often shortened to “states” by experts.
The key size determines how many “rounds” are required to put a plaintext entry through the cipher, thereby converting it to ciphertext.
A 128-bit key requires 10 rounds while a 192-bit key requires 12 rounds. A full 14 rounds are required when a 256-bit key is being used. The longer the key, the more secure the encryption.The trade-off is that the encryption will take much more time.
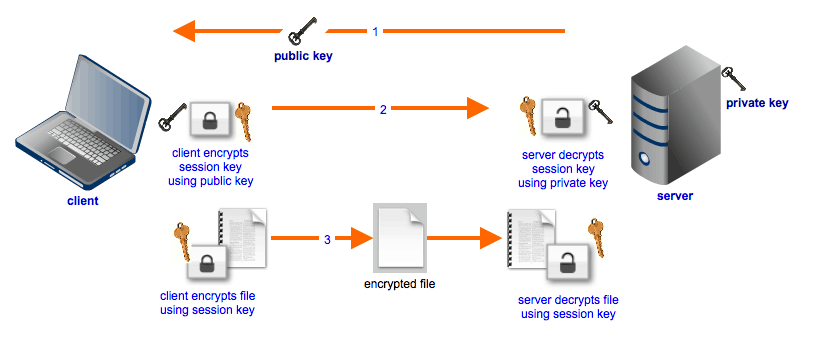
Shouldn’t AES be Asymmetric?
Among the cryptographic community, there is some argument regarding whether symmetric algorithms are easier to break than asymmetric ones. As stated earlier, AES uses the same key to both encrypt and decrypt data, making it a symmetric cipher.
An asymmetric cipher, on the other hand, uses a public key to encrypt files and a separate, private key for decryption. This does add an extra layer of protection, but it does not follow that an asymmetric algorithm is superior in all applications.
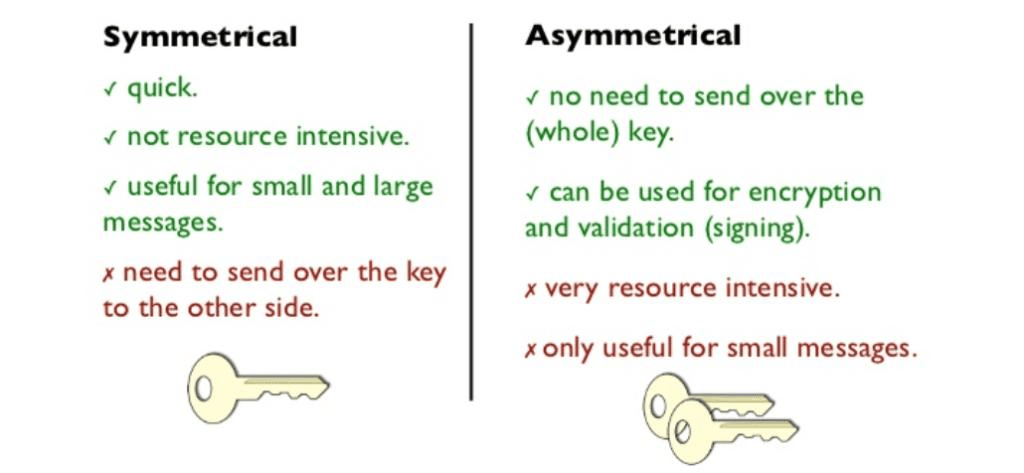
Symmetric algorithms simply operate much faster than asymmetric ones, an important metric for such a widely used cipher.
If you are transferring files, then an asymmetric algorithm may be the way to go. You can give your public key to anyone you like. You wouldn’t even necessarily care if your public key was broadcast to the world.
This is because only your private key is capable of decrypting those files. Anyone who doesn’t have access to your private key can’t look at the data.
How Secure Is AES Encryption?
To date, AES encryption has never been broken the way that DES was way back in 1999. Cryptographers tend to agree that given the current state of technology, it would take billions of years for hackers to break through even a 128-bit key. That is tremendous peace of mind for everyone who relies on AES encryption to protect their files.
As long as the algorithm is properly used, it should continue to protect online data for many years.
Of course, this doesn’t mean that hackers won’t keep trying to find a way through AES encryption. This means that government agencies also are continuously looking for vulnerabilities in the algorithm with hopes of warding off an attack. The more you understand about AES encryption and how it works in conjunction with VPNs, the less likely you are to be the victim of hacking and data leaks.
Did you know that hackers also perform what’s called “footprinting” too? The process involves gathering information about you both online and at home. Secure your network, and secure your home. You never know if the nice man asking for directions is a hacker just trying to get in range so he could use tools to sniff your WiFi packets to get your bank logins.
Sources: