Steganography
Besides cryptography, another method for protecting data involves steganography, which embeds the message inside of a cover object. There are several techniques for steganography including:
- Text steganography
- Image steganography
- Video steganography
- Audio steganography
- Network steganography
Guide to Steganography Types
Below we explained each of the steganography types and explained how good they are at protecting data.
Text Steganography
This refers to the act of hiding information inside of a text file. IT may mean changing the words within the text, changing the format, generating random characters, or using context-free grammar to generate a seemingly readable text. However, the sole purpose is to hide the original message within the cover text.
Image Steganography
You can hide data by also applying a cover object as an image. Widely used for digital steganography, images are mainly the cover source because they have a large number of bits stored in the digital file of the image. The most common ways to hide a message within an image include:
- Masking and filtering
- Least Significant Bit Insertion
- Redundant Pattern Encoding
- Coding and Cosine Transformation
- Encrypt and scatter methods
Audio Steganography
In this method, the secret message is typically hidden within the audio signal, which is changed to a binary sequence of the related audio file. However, this is a much more difficult way to apply a cover object than image and text steganography.
Video Steganography
Any kind of data can be hidden inside of a video format. This means that even a large amount of data can be secretly saved inside of a video file, and since it is moving a high amount of image streaming data already, the difference in file size is hardly detectable.
Network Steganography
This is one of the most secretive ways to use steganography, and it’s a hard method to track. You can hide information within a network control protocol specifically used in TCP, UDP, or ICMP transmissions. It usually involves some form of secret channels classified under the OSI model. In one example, creators can information in the header of a TCP packet in some of the fields that are optional.
How Steganography Matters for Cryptology
How Steganography Matters for Cryptology – Stenography is an alternative technique used in Cryptography to hide plain text in complex structures such as text files, image files, audio files, and networks.
What is Steganography
Steganography – Stenography is the practice of communicating through messages hidden in other structures such as images. They will only be apparent to a trained eye.
This is a basic model depicting steganography:

In this example, both the the cover file and hidden message are fed into a steganographic encoding application as input. The steganopgraphic function represented by f(X,M,K) hides the secret message inside of a cover file. The result is a stego object that looks similar to the actual cover file, but the differences cannot be seen by the naked eye. This completes the process of encoding. To see the hidden message, the stego object must be fed into a steganographic decoder.
History of Steganography
The word steganography actually comes from two Greek words, including steganos and graphia. Steganos is the Greek word for “covered” and “graphia” is the main word for writing. Since it is an ancient practice, steganography has evolved over thousands of years, taking on many different forms to keep information and communications as private as possible.
The first use of steganography can be linked back to 440 BC. At this time, people wrote messages on wood, then covered it with wax in order to cover up the hidden message.
Romans also used various invisible inks, which needed unique light sources to see hidden messages.
In World War II, Germans used microdots, which were entire documents and images reduced to the size of a small dot. These were attached to normal documents and needed a magnifying glass to read.
Null ciphers were also developed as a way to hide a message unencrypted in a perceived normal message.
What is Modern Steganography
Modern Steganography – Modern stenography has moved to more innovative and complex techniques that use digital media as cover messages in contrast to more straight-forward methods like text files.
How is Steganography Different From Cryptography
The central point of cryptography and steganography is the same. Both are used to protect sensitive information or “the message” from an unauthorized third party. However, they use completely different methods to protect this data.
Cryptography refers to transforming the raw text over to a ciphertext, which cannot be understand without the use of a key. If someone does intercept an encrypted message, they can easily see that an encryption method has been applied. An important part of cryptography is mathematics.
However, steganography does not change the format of the information, but it does conceal the message.
Here is a quick table to see the comparison side-by-side:
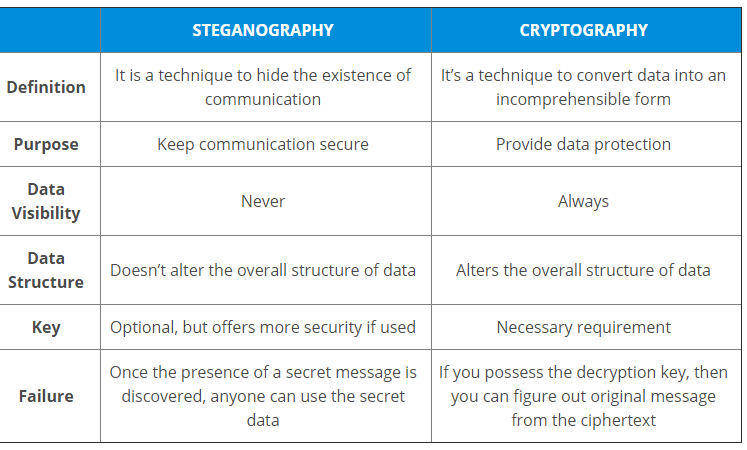
Since the message is never shown in steganography, it is thought to be more discreet than cryptography, at least for sending very sensitive information. However, the hidden message is easy to discover once the presence of the secret is known.
Keys are also optional in steganography, but they are required with cryptography algorithms. An important aspect of cryptography is cryptanalysis.
