Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
Substitution Ciphers
Ciphers are used in a variety of technical applications with varying degrees of complexity. To simply put it, the more complex the cipher, the more secure the stored value will be.
The affine cipher is one of the wider-known, lesser-complex ciphers that provide a good introduction to monoalphabetic substitutions.
In other words, the affine cipher can teach those interested in how substitution ciphers work.
Types of Substitution Ciphers
Through an algorithm, substitution ciphers replace characters with a new “ciphered” character to disguise the original message.
As the algorithm is a basic mathematical formula, the actual encryption is quite weak and is easy to decipher. There are multiple types of substitution ciphers we will discuss today.
Simple Substitution
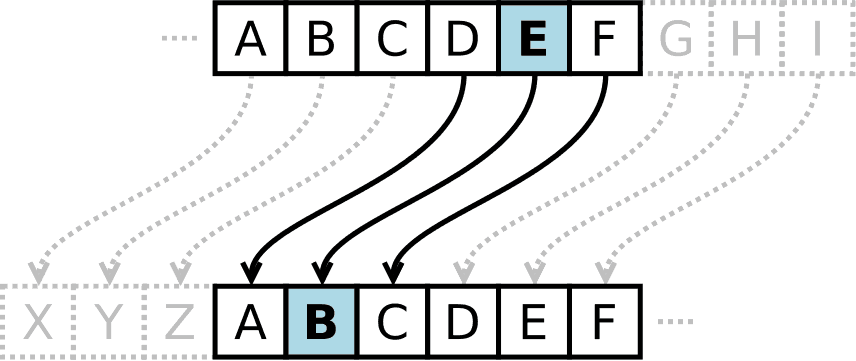
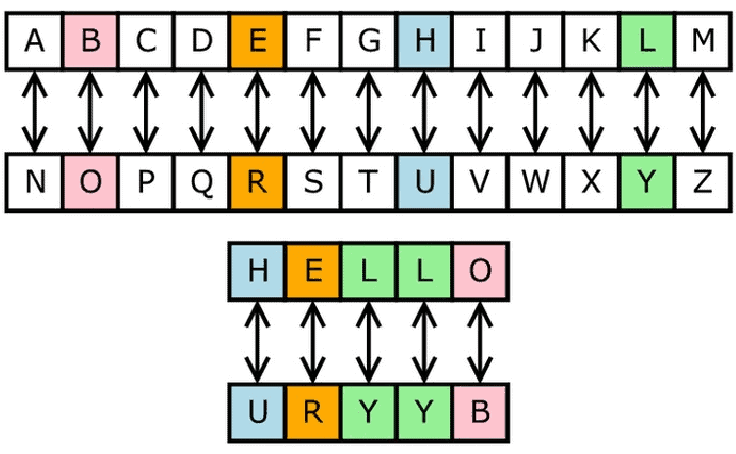
The most basic type of substitution cipher is called a simple substitution. In these ciphers, single letters are substituted by another letter. Ciphers often use a key that defines a shift in the alphabet.
For instance, if you used a shift of 23 characters to the right, a character of A would correspond to a cipher character of X.
Two of the most common substitution ciphers are the Atbash Cipher and the Caesar Cipher. Other examples include the Affine Cipher and Baconian Cipher.
Homophonic Substitution

Homophonic ciphers were designed to be more difficult to crack than a basic substitution cipher by utilizing homophony. Letters in the plaintext can be replaced by several different characters.
These characters may be uppercase or lowercase letters or even numbers.
The more frequent a letter is, the more options of cipher characters it will have. For instance, the letter O will have more cipher characters than the letter X.
This characteristic defines the cipher and makes cryptanalysis more difficult. Nomenclator ciphers and Beale Ciphers can both be based on homophonic ciphers, though not all are.
Polyalphabetic Substitution
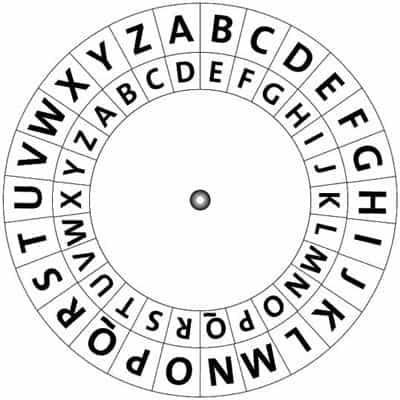
Polyalphabetic ciphers take the difficulty up even further. These ciphers utilize multiple alphabets to encrypt plaintext. Typically, the cipher will make use of a tableau—a written table of the various alphabets used.
These tables can have several alphabets and may even contain up to 26 to create a 26 x 26 table. Different types of these ciphers use various means to determine which alphabet to use to encrypt the plaintext.
One of the most well-known polyalphabetic ciphers is the Vigenère Cipher which uses a 26×26 tableau, also called a tabula recta. Additional ciphers include the Enigma Cipher, Beaufort Cipher, and Autokey Cipher.
Polygraphic Substitution
A more unique style of substitution is employed by polygraphic ciphers. Rather than substitute individual letters, these ciphers substitute groups of characters together.
This makes the ciphertext more complex to analyze as the frequency of the pairs is flatter than when individual letters are substituted.
A classic polygraphic cipher is the Hill Cipher. Here, the encryption is based on linear algebra. Other examples include the Four-Square Cipher and the Playfair Cipher.
The Bottom Line
We talked about the basics of some of the more common types of ciphers. Each category has it’s pros and cons, but as the technology they are getting easier to decipher.
If you are interested in learning more about things like Classical Ciphers or if you are looking for an internet privacy guide, take a look at our website!