Privacy Canada is community-supported. We may earn a commission when make a purchase through one of our links. Learn more.
One Time Pad
Towards the end of the 19th century, it was becoming fairly obvious that simple substitution ciphers that were vulnerable to frequency analysis were no longer secure. How could they transmit a message without it’s contents being vulnerable to inspection, while still being able to be decrypted once they reached their destination? The answer is randomness.
Let’s consider a modified version of the Vigenère cipher as an example. Instead of performing alphabet shifts on each character in the plaintext via a key, we shift every character in the plaintext a random amount – with each of these random shift amounts becoming the resulting key. This results in a completely random key the exact same length as the original plaintext. This means that across the entire message, there can be no structure deduced from the frequency of characters, as the key itself was entirely randomly created. This type of encryption is called the one time pad, and the benefits don’t stop there.
With each character now having it’s own individual and random shift amount, the keyspace grows exponentially for each character in the message. Let’s say we were to encrypt the name “Alice” with a one time pad. That’s 5 letters – so to brute force it you would have to try a whole lot of possibilities:
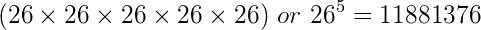
However, this would simply brute force the search space. You still wouldn’t know *which* of the millions of attempts you tried were correct, because (due to the randomness of the one time pad) it’s possible that attempting to decrypt the message with an incorrect key, could potentially give a coherent *but incorrect* result. Because of this, while being a relatively simple encryption technique, the one time pad is considered unbreakable if used properly.
There are however, downsides to the one time pad that should always be considered. The key size is always identical to the size of the message – which for long messages eventually becomes a lot of data to manage and a long encryption/decryption process. It also relies on a source of randomness, which can be exploited if not generated in a truly random fashion.




